It’s nice and refreshing to sweep through basic challenges, on the flip side, I’m counting this entire post as 1 flag ![]()
Table of Contents 
| Challenges | Summary |
|---|---|
| Level 0 | ssh |
| Level 1 | file called “-“ |
| Level 2 | file with spaces in the name |
| Level 3 | ls -la |
| Level 4 | file |
| Level 5 | ls piped into grep |
| Level 6 | find |
| Level 7 | cat piped into grep |
| Level 8 | sort piped into uniq |
| Level 9 | strings piped into grep |
| Level 10 | base64 decode |
| Level 11 | cat piped into tr |
| Level 12 | xxd reverse, decompress gzip, bzip, and tar |
| Level 13 | ssh rsa connect |
| Level 14 | telnet |
| Level 15 | openssl connect |
| Level 16 | nmap |
| Level 17 | diff |
| Level 18 | ssh bypass ~/.bashrc
|
| Level 19 | what is a setuid binary |
| Level 20 | netcat and screen |
| Level 21 | cron |
| Level 22 | simple shellscript |
| Level 23 | analyzing a shellscript |
| Level 24 | making a shellscript for bruteforcing |
| Level 25 |
more to vi exploit |
| Level 26 | what is a setuid binary, after spawning a shell |
| Level 27 | git clone |
| Level 28 | git log |
| Level 29 | git packed-refs |
| Level 30 | git tag |
| Level 31 | git push |
| Level 32 | shell positional arguments |
| Level 33 | ending |
Level 0 
Problem 
The password for the next level is stored in a file called readme located in the home directory.
Hint 
ls, cd, cat, file, du, find
Solution 
Connect with ssh with the ssh command.
ssh bandit0@bandit.labs.overthewire.org -p 2220
Input password bandit0 then cat the readme file

Flag
boJ9jbbUNNfktd78OOpsqOltutMc3MY1
Level 1 
Problem 
The password for the next level is stored in a file called - located in the home directory
Hint 
Google Search for “dashed filename”
ls, cd, cat, file, du, find
Solution 
Googled, found this
cat ./-
Flag
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
Level 2 
Problem 
The password for the next level is stored in a file called spaces in this filename located in the home directory.
Hint 
ls, cd, cat, file, du, find
Solution 
We can use tab completion or escape sequences.
bandit2@bandit:~$ ls -l
total 4
-rw-r----- 1 bandit3 bandit2 33 Oct 16 2018 spaces in this filename
bandit2@bandit:~$ cat spaces\ in\ this\ filename
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
bandit2@bandit:~$
Flag
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
Level 3 
Problem 
The password for the next level is stored in a hidden file in the inhere directory.
Hint 
ls, cd, cat, file, du, find
Solution 
Description for ls flags:
-
-lmeans show as a list -
-ameans all, including hidden files
bandit3@bandit:~$ ls
inhere
bandit3@bandit:~$ cd inhere/
bandit3@bandit:~/inhere$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Oct 16 2018 .
drwxr-xr-x 3 root root 4096 Oct 16 2018 ..
-rw-r----- 1 bandit4 bandit3 33 Oct 16 2018 .hidden
bandit3@bandit:~/inhere$ cat .hidden
pIwrPrtPN36QITSp3EQaw936yaFoFgAB
bandit3@bandit:~/inhere$
Flag
pIwrPrtPN36QITSp3EQaw936yaFoFgAB
Level 4 
Problem 
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
Hint 
ls, cd, cat, file, du, find
Solution 
bandit4@bandit:~/inhere$ file ./*
./-file00: data
./-file01: data
./-file02: data
./-file03: data
./-file04: data
./-file05: data
./-file06: data
./-file07: ASCII text
./-file08: data
./-file09: data
bandit4@bandit:~/inhere$ cat ./-file07
koReBOKuIDDepwhWk7jZC0RTdopnAYKh
bandit4@bandit:~/inhere$
Flag
koReBOKuIDDepwhWk7jZC0RTdopnAYKh
Level 5 
Problem 
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties: human-readable, 1033 bytes in size, not executable
Hint 
ls, cd, cat, file, du, find
Solution 
bandit5@bandit:~/inhere$ ls -la ./* | grep 1033 -7
./maybehere07:
total 56
drwxr-x--- 2 root bandit5 4096 Oct 16 2018 .
drwxr-x--- 22 root bandit5 4096 Oct 16 2018 ..
-rwxr-x--- 1 root bandit5 3663 Oct 16 2018 -file1
-rwxr-x--- 1 root bandit5 3065 Oct 16 2018 .file1
-rw-r----- 1 root bandit5 2488 Oct 16 2018 -file2
-rw-r----- 1 root bandit5 1033 Oct 16 2018 .file2
-rwxr-x--- 1 root bandit5 3362 Oct 16 2018 -file3
-rwxr-x--- 1 root bandit5 1997 Oct 16 2018 .file3
-rwxr-x--- 1 root bandit5 4130 Oct 16 2018 spaces file1
-rw-r----- 1 root bandit5 9064 Oct 16 2018 spaces file2
-rwxr-x--- 1 root bandit5 1022 Oct 16 2018 spaces file3
./maybehere08:
bandit5@bandit:~/inhere$ cat ./maybehere07/.file2
DXjZPULLxYr17uwoI01bNLQbtFemEgo7
Flag
DXjZPULLxYr17uwoI01bNLQbtFemEgo7
Level 6 
Problem 
The password for the next level is stored somewhere on the server and has all of the following properties: owned by user bandit7, owned by group bandit6, 33 bytes in size
Hint 
ls, cd, cat, file, du, find, grep
Solution 
We find out what the filename is first using grep and some regex, since the file can be anywhere lets go to / and start lsing from there.
bandit6@bandit:/$ cd /
bandit6@bandit:/$ ls -la ./*/*/*/* | grep "bandit7.*bandit6.*33"
...
-rw-r----- 1 bandit7 bandit6 33 Oct 16 2018 bandit7.password
...
Now we know the filename is bandit7.password, let’s use find to find it.
bandit6@bandit:/$ find / -name "bandit7.password"
...
/var/lib/dpkg/info/bandit7.password
...
bandit6@bandit:/$ cat /var/lib/dpkg/info/bandit7.password
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
Flag
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
Level 7 
Problem 
The password for the next level is stored in the file data.txt next to the word millionth
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution 
If you just cat data.txt the output will be big and we will recognize a format of “some_word
bandit7@bandit:~$ cat data.txt | grep "millionth" -1
cannonball's AT5sruEPDKWFxOFI9a7M38diYBIkbNQ4
millionth cvX2JJa4CFALtqS87jk27qwqGhBM9plV
comprehend FKVbjZbVgb0d2RU2DlCqSW049xMITQkB
Flag
cvX2JJa4CFALtqS87jk27qwqGhBM9plV
Level 8 
Problem 
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution 
Getting a bit harder now, lets look at man uniq, in the description section we’ll find this.
Note: 'uniq' does not detect repeated lines unless they are adjacent. You may want to sort the input first, or use 'sort -u' without 'uniq'.
Let’s test our what sort does.
bandit8@bandit:~$ sort data.txt
...
07iR6PwHwihvQ3av1fqoRjICCulpoyms
07iR6PwHwihvQ3av1fqoRjICCulpoyms
0ob6rCn4D4jQ6KCiaT5hmOdWFrm2quR1
0ob6rCn4D4jQ6KCiaT5hmOdWFrm2quR1
0ob6rCn4D4jQ6KCiaT5hmOdWFrm2quR1
...
Ok so sort just sorts the file and prints into stdout, now we go back to man uniq and we find this flag/switch
...
-u, --unique
only print unique lines
...
Now that we have identical lines adjacent (after we sort it), we can then use uniq -u.
bandit8@bandit:~$ sort data.txt | uniq -u
UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
Flag
UsvVyFSfZZWbi6wgC7dAFyFuR6jQQUhR
Level 9 
Problem 
The password for the next level is stored in the file data.txt in one of the few human-readable strings, beginning with several ‘=’ characters.
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution 
If we cat data.txt we’ll see a bunch of binary data, so let’s use strings to just print out the human-readable strings and find ones with a = in them using grep.
bandit9@bandit:~$ strings data.txt | grep "="
2========== the
========== password
>t= yP
rV~dHm=
========== isa
=FQ?P\U
= F[
pb=x
J;m=
=)$=
========== truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
iv8!=
Flag
truKLdjsbJ5g7yyJ2X2R0o3a5HQJFuLk
Level 10 
Problem 
The password for the next level is stored in the file data.txt, which contains base64 encoded data
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution 
We base64 decode the data
bandit10@bandit:~$ cat data.txt | base64 -d
The password is IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
Flag
IFukwKGsFW8MOq3IRFqrxE1hxTNEbUPR
Level 11 
Problem 
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd
Solution 
We use tr to translate the uppercase chars into the shifted uppercase chars, 13 chars after ‘A’ is ‘N` so that will be our new A, and when we reach ‘Z’ we loop back to ‘A’. Same thing with the lowercase chars.
bandit11@bandit:~$ cat data.txt | tr '[A-Za-z]' '[N-ZA-Mn-za-m]'
The password is 5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
Flag
5Te8Y4drgCRfCx8ugdwuEX8KFC6k2EUu
Level 12 
Problem 
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed.
Hint 
grep, sort, uniq, strings, base64, tr, tar, gzip, bzip2, xxd, mkdir, cp, mv, file
Solution 
First, let’s move to a temp dir /temp/asd and bring the file with us.
bandit12@bandit:/tmp/asd$ cp /home/bandit12/data.txt ./
bandit12@bandit:/tmp/asd$ ls
data.txt
Let’s see what’s in data.txt.
bandit12@bandit:/tmp/asd$ file data.txt
data.txt: ASCII text
bandit12@bandit:/tmp/asd$ cat data.txt
00000000: 1f8b 0808 d7d2 c55b 0203 6461 7461 322e .......[..data2.
00000010: 6269 6e00 013c 02c3 fd42 5a68 3931 4159 bin..<...BZh91AY
...
Now let’s reverse it using xxd and direct the output into a file instead of stdout.
bandit12@bandit:/tmp/asd$ xxd -r data.txt
�▒▒h��6��@4▒bi���h▒91AY&SY���������ϟ�����������������9��
�mF�h�h44
▒��B��,0�� ��4@�����@2▒C@h�� �
�ɋ�^-K�����}�\,�▒ǿ�}E�F�_!r�U�g?E�i��9x��TB@�lȲ���BF.hM�SC4�V�F��R�Br"�<(Hت$ $���KBs��%l▒~�_�▒ݿ����g�zM�w�#P"2@������
��\��WQO4�p�i�����S�#&��/�#��[j▒�<D�uԐ^_�H.�-��wAt
�[��UP�G�CP��&:�2�*�)�\�������H�
�\�7��w<
bandit12@bandit:/tmp/asd$ xxd -r data.txt > binarydata
Now we look at what the output file is.
bandit12@bandit:/tmp/asd$ ls
binarydata data.txt
bandit12@bandit:/tmp/asd$ file binarydata
binarydata: gzip compressed data, was "data2.bin", last modified: Tue Oct 16 12:00:23 2018, max compression, from Unix
So it’s a gzip archive, let’s rename it then decompress it.
bandit12@bandit:/tmp/asd$ cp binarydata data.gz
bandit12@bandit:/tmp/asd$ ls
binarydata data.gz data.txt
bandit12@bandit:/tmp/asd$ gzip -d data.gz
bandit12@bandit:/tmp/asd$ ls
binarydata data data.txt
Now we see what’s next.
bandit12@bandit:/tmp/asd$ file data
data: bzip2 compressed data, block size = 900k
It’s a bzip archive now, let’s decompress it then see what we have next.
bandit12@bandit:/tmp/asd$ mv data data.bz2
bandit12@bandit:/tmp/asd$ bzip2 -d data.bz2
bandit12@bandit:/tmp/asd$ ls
binarydata data data.txt
bandit12@bandit:/tmp/asd$ file data
data: gzip compressed data, was "data4.bin", last modified: Tue Oct 16 12:00:23 2018, max compression, from Unix
Another gzip.
bandit12@bandit:/tmp/asd$ gzip -d data.gz
bandit12@bandit:/tmp/asd$ ls
binarydata data data.txt
bandit12@bandit:/tmp/asd$ file data
data: POSIX tar archive (GNU)
Now it’s a tar archive, the flag to decompress it is a bit different.
bandit12@bandit:/tmp/asd$ cp data data.tar
bandit12@bandit:/tmp/asd$ tar -xvf data.tar
data5.bin
After this, it’s basically these 3 archive formats repeated over and over, in total you have to
- determine the
file, - rename it accordingly, then
- decompress it
for a total of 9 times, then you’ll get this string.
bandit12@bandit:/tmp/asd$ file data
data: ASCII text
bandit12@bandit:/tmp/asd$ cat data
The password is 8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
Flag
8ZjyCRiBWFYkneahHwxCv3wb2a1ORpYL
Level 13 
Problem 
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
Hint 
ssh, telnet, nc, openssl, s_client, nmap
Solution 
Let’s look for a private ssh key.
bandit13@bandit:~$ ls -la
total 24
drwxr-xr-x 2 root root 4096 Oct 16 2018 .
drwxr-xr-x 41 root root 4096 Oct 16 2018 ..
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
-rw-r----- 1 bandit14 bandit13 1679 Oct 16 2018 sshkey.private
bandit13@bandit:~$ cat sshkey.private
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAxkkOE83W2cOT7IWhFc9aPaaQmQDdgzuXCv+ppZHa++buSkN+
gg0tcr7Fw8NLGa5+Uzec2rEg0WmeevB13AIoYp0MZyETq46t+jk9puNwZwIt9XgB
...
kAWpXbv5tbkkzbS0eaLPTKgLzavXtQoTtKwrjpolHKIHUz6Wu+n4abfAIRFubOdN
/+aLoRQ0yBDRbdXMsZN/jvY44eM+xRLdRVyMmdPtP8belRi2E2aEzA==
-----END RSA PRIVATE KEY-----
Looks like this is the ssh private key we’re going to be using to ssh into bandit14, we specify the key with -i. We then ssh into localhost as hinted in the problem description.
bandit13@bandit:~$ ssh bandit14@localhost -i ~/sshkey.private
...
bandit14@bandit:~$ cat /etc/bandit_pass/bandit14
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Flag
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Level 14 
Problem 
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
Hint 
ssh, telnet, nc, openssl, s_client, nmap
Solution 
Since the problem desc didn’t specify how to send the data (the current password), we’ll guess that it’s through telnet by looking at the hint.
bandit14@bandit:~$ telnet localhost 30000
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
4wcYUJFw0k0XLShlDzztnTBHiqxU3b3e
Correct!
BfMYroe26WYalil77FoDi9qh59eK5xNr
Connection closed by foreign host.
bandit14@bandit:~$
Flag
BfMYroe26WYalil77FoDi9qh59eK5xNr
Level 15 
Problem 
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Hint 
ssh, telnet, nc, openssl, s_client, nmap
Solution 
Clicking on the link provided in the hint, it has a guide on how to connect with openssl.
bandit15@bandit:~$ openssl s_client -connect localhost:30001
...
BfMYroe26WYalil77FoDi9qh59eK5xNr
Correct!
cluFn7wTiGryunymYOu4RcffSxQluehd
closed
bandit15@bandit:~$
Full openssl output
bandit15@bandit:~$ openssl s_client -connect localhost:30001
CONNECTED(00000003)
depth=0 CN = localhost
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = localhost
verify return:1
---
Certificate chain
0 s:/CN=localhost
i:/CN=localhost
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICBjCCAW+gAwIBAgIEYo1NxTANBgkqhkiG9w0BAQUFADAUMRIwEAYDVQQDDAls
b2NhbGhvc3QwHhcNMjAwMTA1MTQzNTU4WhcNMjEwMTA0MTQzNTU4WjAUMRIwEAYD
VQQDDAlsb2NhbGhvc3QwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAKF4u2eu
a8VipZPviX0hfNiCnaD2ojAffdBhKTy1bmZSNRuHPBDnU7z8rblNSknSjCITda1C
GEAI8ZktRbtLpBTbYeTgqPN/EiN5UIRMKbU6P2O93zNFPBsmyfQLrgt+DSLnsxlB
i/yYyT7WLdtNVBpgwRwkqi9K7dk9vf9waswLAgMBAAGjZTBjMBQGA1UdEQQNMAuC
CWxvY2FsaG9zdDBLBglghkgBhvhCAQ0EPhY8QXV0b21hdGljYWxseSBnZW5lcmF0
ZWQgYnkgTmNhdC4gU2VlIGh0dHBzOi8vbm1hcC5vcmcvbmNhdC8uMA0GCSqGSIb3
DQEBBQUAA4GBAJECW6IB3Ria4xG002BqD3zEbtmrDlK6nmJq+uQ4eJ6cT18o9REb
npy/lFzlv2LfcrYAnuAp6Fh89MKaYjNzJURjRQ9RkmcYgQJa1n+OBkATb7V+84/a
k9PDRkscxdNFMGBSvzFD33XZ5lbaGdrwCPyoxenoYghV/753wffN7J6H
-----END CERTIFICATE-----
subject=/CN=localhost
issuer=/CN=localhost
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 1019 bytes and written 269 bytes
Verification error: self signed certificate
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 1024 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 4595845EEA811B7DF28C6F51178285E2DF9373646EA7CF76955A8DE624AD46EF
Session-ID-ctx:
Master-Key: 567E0B85A0BEA02DE942BB44C7C9C65FCCD44ED70C370292F3A3A0668EFA11117D1A48DD77A49A58DDA592D66A5A2207
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 56 e9 4e 87 6a 28 48 d0-13 42 5f b9 61 b0 dd d0 V.N.j(H..B_.a...
0010 - dc 2f 06 c8 62 cf 91 d8-f2 84 b9 58 37 7e d0 42 ./..b......X7~.B
0020 - 29 c4 0e 9b 80 33 a5 c0-db ed ce e3 8f b0 85 9f )....3..........
0030 - 4c 72 a4 37 e7 21 47 0c-f0 a4 9a 9b b7 8f 89 0e Lr.7.!G.........
0040 - de b0 60 1a 47 7d c8 49-4c 74 7e b0 b1 ea ab b5 ..`.G}.ILt~.....
0050 - 7f cf a3 a0 32 43 9f 97-6d 88 1d d9 bd c4 4a 83 ....2C..m.....J.
0060 - 7b d5 0b e5 84 32 cb f8-e3 f9 01 20 7d 07 a5 0e {....2..... }...
0070 - b4 7c 5f aa 95 01 7f 05-09 f4 cf d9 20 1c 86 9f .|_......... ...
0080 - 47 e9 dc f3 77 5c fe 32-39 ef 12 bc e5 60 b6 6f G...w\.29....`.o
0090 - 5a 46 af 52 55 8f 64 32-84 12 03 10 57 28 44 ee ZF.RU.d2....W(D.
Start Time: 1582032731
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Extended master secret: yes
---
BfMYroe26WYalil77FoDi9qh59eK5xNr
Correct!
cluFn7wTiGryunymYOu4RcffSxQluehd
closed
bandit15@bandit:~$
Flag
cluFn7wTiGryunymYOu4RcffSxQluehd
Level 16 
Problem 
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
Hint 
ssh, telnet, nc, openssl, s_client, nmap
Solution 
Let’s nmap the machine, -sV checks for the actual service that’s running on the port, -p specifies the ports to scan.
bandit16@bandit:~$ nmap localhost -sV -p 31000-32000
...
PORT STATE SERVICE VERSION
31518/tcp open ssl/echo
31790/tcp open ssl/unknown
...
Full nmap output
bandit16@bandit:~$ nmap localhost -sV -p 31000-32000
Starting Nmap 7.40 ( https://nmap.org ) at 2020-02-18 14:44 CET
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00026s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
31518/tcp open ssl/echo
31790/tcp open ssl/unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31790-TCP:V=7.40%T=SSL%I=7%D=2/18%Time=5E4BEA41%P=x86_64-pc-linux-g
SF:nu%r(GenericLines,31,"Wrong!\x20Please\x20enter\x20the\x20correct\x20cu
SF:rrent\x20password\n")%r(GetRequest,31,"Wrong!\x20Please\x20enter\x20the
SF:\x20correct\x20current\x20password\n")%r(HTTPOptions,31,"Wrong!\x20Plea
SF:se\x20enter\x20the\x20correct\x20current\x20password\n")%r(RTSPRequest,
SF:31,"Wrong!\x20Please\x20enter\x20the\x20correct\x20current\x20password\
SF:n")%r(Help,31,"Wrong!\x20Please\x20enter\x20the\x20correct\x20current\x
SF:20password\n")%r(SSLSessionReq,31,"Wrong!\x20Please\x20enter\x20the\x20
SF:correct\x20current\x20password\n")%r(TLSSessionReq,31,"Wrong!\x20Please
SF:\x20enter\x20the\x20correct\x20current\x20password\n")%r(Kerberos,31,"W
SF:rong!\x20Please\x20enter\x20the\x20correct\x20current\x20password\n")%r
SF:(FourOhFourRequest,31,"Wrong!\x20Please\x20enter\x20the\x20correct\x20c
SF:urrent\x20password\n")%r(LPDString,31,"Wrong!\x20Please\x20enter\x20the
SF:\x20correct\x20current\x20password\n")%r(LDAPSearchReq,31,"Wrong!\x20Pl
SF:ease\x20enter\x20the\x20correct\x20current\x20password\n")%r(SIPOptions
SF:,31,"Wrong!\x20Please\x20enter\x20the\x20correct\x20current\x20password
SF:\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 88.20 seconds
bandit16@bandit:~$
We found 2 ports, the first one looks like it’s only running echo, so let’s try out the 2nd one.
bandit16@bandit:~$ openssl s_client -connect localhost:31790
...
cluFn7wTiGryunymYOu4RcffSxQluehd
Correct!
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
...
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
closed
bandit16@bandit:~$
Full openssl output
bandit16@bandit:~$ openssl s_client -connect localhost:31790
CONNECTED(00000003)
depth=0 CN = localhost
verify error:num=18:self signed certificate
verify return:1
depth=0 CN = localhost
verify return:1
---
Certificate chain
0 s:/CN=localhost
i:/CN=localhost
---
Server certificate
-----BEGIN CERTIFICATE-----
MIICBjCCAW+gAwIBAgIEGPttrzANBgkqhkiG9w0BAQUFADAUMRIwEAYDVQQDDAls
b2NhbGhvc3QwHhcNMjAwMjA5MjA0NzE5WhcNMjEwMjA4MjA0NzE5WjAUMRIwEAYD
VQQDDAlsb2NhbGhvc3QwgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBAPiElqK1
D097ZCNDgKFxqX1ZUUpFfuoiDSP2dw5KrIruaTQMmfqCxo6dSHvkj1sF//YRI28k
BGyu9pE3zLO45uk4PrjoORYLoQjTCb61oVZLECCOIG21WQUbrhjW4zlZGmtWrqw6
zGLk7dZ8MeYHVSvK0n3Ar45hVedpsLC618ZTAgMBAAGjZTBjMBQGA1UdEQQNMAuC
CWxvY2FsaG9zdDBLBglghkgBhvhCAQ0EPhY8QXV0b21hdGljYWxseSBnZW5lcmF0
ZWQgYnkgTmNhdC4gU2VlIGh0dHBzOi8vbm1hcC5vcmcvbmNhdC8uMA0GCSqGSIb3
DQEBBQUAA4GBADJEAM0VceCYaqhfzpzkzf6dhCIWbb/8P+51Wxw24sn9iLHxdqYe
1WNfxtQb8IYb3q/6JJDJ3d6plNKmFMkFBe5AiN05PCDeMymkTv8vlKj18UNR/4GL
AH1aFGcEYVXkwX0Kl844muUrK7S0AbOvcHmzzA++qTmfB1UK264G0iAH
-----END CERTIFICATE-----
subject=/CN=localhost
issuer=/CN=localhost
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 1019 bytes and written 269 bytes
Verification error: self signed certificate
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 1024 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 2D6FB7CB3F0A2275C16BC10508A2CC1EB3B56BD2FD86FB252AD0EBEE4BA5B782
Session-ID-ctx:
Master-Key: 884B8211F71BB5F4864CD99B1D63711FAFAAAB584A547B22DF2D7C1854233D1FF3149D8D8A18B3EF96614A79A6656532
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 7200 (seconds)
TLS session ticket:
0000 - 9f 82 12 97 ac 31 10 5b-65 4b 5d fb 71 e9 e8 02 .....1.[eK].q...
0010 - bf 90 eb ef ca b7 bd a1-a2 94 6a 3b 73 13 7b ec ..........j;s.{.
0020 - 41 22 7b 37 40 a2 65 2e-0f 89 90 bb 33 1c 3e 28 A"{7@.e.....3.>(
0030 - 00 9d 1c 0e e6 5b 34 8d-60 ce bf f6 29 15 a3 ec .....[4.`...)...
0040 - 4e ac bb 26 a8 a5 21 49-a0 ae 7f 16 2b 4c de 04 N..&..!I....+L..
0050 - ac a4 c5 63 27 69 69 3c-9d e8 f0 de 21 5d de d7 ...c'ii<....!]..
0060 - 56 b0 2f 0b 1c 9b 11 70-77 67 6e e3 a0 6b 8c 66 V./....pwgn..k.f
0070 - d3 e1 68 63 87 4c a6 6f-c9 0b f5 47 ae 2b 2c 6e ..hc.L.o...G.+,n
0080 - 87 78 a7 ba 9a e3 93 24-67 c1 39 da 16 a7 60 96 .x.....$g.9...`.
0090 - e4 a4 a0 ca b5 9e ca bd-ad 2e 80 6b ab 02 dd 0f ...........k....
Start Time: 1582033598
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Extended master secret: yes
---
cluFn7wTiGryunymYOu4RcffSxQluehd
Correct!
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
closed
bandit16@bandit:~$
Flag
The RSA key we got from SSL, which we will use to connect to the next level.
Level 17 
Problem 
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
Hint 
cat, grep, ls, diff
Solution 
First we take the RSA key we got from the previous level, paste it into a file, and then change it’s privileges to avoid this error.
$ ssh bandit17@bandit.labs.overthewire.org -p 2220 -i ./bandit17
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for './bandit17' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "./bandit17": bad permissions
bandit17@bandit.labs.overthewire.org's password:
[1] 10758 quit ssh bandit17@bandit.labs.overthewire.org -p 2220 -i ./bandit17
Now to change the privileges.
$ ls -la
...
-rw-r--r-- 1 root root 1675 Feb 18 14:05 bandit17
...
$ chmod 400 bandit17
$ ls -la
...
-r-------- 1 root root 1675 Feb 18 14:05 bandit17
...
Now we can actually connect to the bandit17 level.
$ ssh bandit17@bandit.labs.overthewire.org -p 2220 -i ./bandit17
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
...
bandit17@bandit:~$
Now on the the actual problem, we’ll use diff to find differences between 2 files.
bandit17@bandit:~$ diff passwords.old passwords.new
42c42
< hlbSBPAWJmL6WFDb06gpTx1pPButblOA
---
> kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
Flag
kfBf3eYk5BPBRzwjqutbbfE887SVc5Yd
Level 18 
Problem 
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
Hint 
ssh, ls, cat
Solution 
A bit on the frustrating side, if we login as usual, we just get kicked out. But then, google to the rescue! Found this. Let’s take a look at man ssh and see what parameters it actually accepts.
ssh [-1246AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-e escape_char] [-F configfile]
[-I pkcs11] [-i identity_file] [-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port]
[-Q query_option] [-R address] [-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]] [user@]hostname [command]
We see that after [user@]hostname there’s a [command], since ~/.bashrc only applies for bash shells, we can invoke an sh shell instead so we don’t get kicked by the ~/.bashrc script.
Let’s also look at -t in man ssh.
If an interactive session is requested ssh by default will only request a pseudo-terminal (pty) for interactive sessions when the client has one.
The flags -T and -t can be used to override this behaviour.
It looks like by using -t we are requesting a “real” shell instead of a pseudo one.
$ ssh -t bandit18@bandit.labs.overthewire.org -p 2220 sh
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org's password:
$ ls
readme
$ cat readme
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
Alternatively we can still use bash but with the --norc flag/switch to not run ~/.bashrc when we get to our shell.
ssh -t bandit18@bandit.labs.overthewire.org -p 2220 "bash --norc"
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org's password:
bash-4.4$ ls
readme
bash-4.4$ cat readme
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
Flag
IueksS7Ubh8G3DCwVzrTd8rAVOwq3M5x
Level 19 
Problem 
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
Hint 
Solution 
We can see that the setuid bit is true from the letter s on the file privileges where x is supposed to be (on the bandit20-do executable file).
bandit19@bandit:~$ ls -la
total 28
drwxr-xr-x 2 root root 4096 Oct 16 2018 .
drwxr-xr-x 41 root root 4096 Oct 16 2018 ..
-rwsr-x--- 1 bandit20 bandit19 7296 Oct 16 2018 bandit20-do
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
Let’s see what this does
bandit19@bandit:~$ ./bandit20-do
Run a command as another user.
Example: ./bandit20-do id
Looks like it just runs a command as the user bandit20, the owner of the file, as described in the wiki page referred to in the hint. Now the user bandit20 should have access to it’s own level’s password, right? Let’s try it out.
bandit19@bandit:~$ ./bandit20-do cat /etc/bandit_pass/bandit20
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Flag
GbKksEFF4yrVs6il55v6gwY5aVje5f0j
Level 20 
Problem 
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
Hint 
ssh, nc, cat, bash, screen, tmux, Unix ‘job control’ (bg, fg, jobs, &, CTRL-Z, …)
Solution 
Understanding the problem desc is the tricky part here. suconnect will not listen for connections, it will connect instead. So we need something to listen while we execute suconnect and connect to it, simplest solution would be nc. But we usually need 2 terminals for a back and forth communication, so let’s learn about screen which could split 1 terminal into multiple sub-terminals.

In the gif, I first opened up screen, then I split the terminal screen into 2 vertically, then (notice the “0 bash” and “1 bash” in the bottom of the sub-terminal screens indicating different “instances” of screen) I opened another screen so I can then have 2 of them running at the same time. So one screen will run nc and listen for connections on a port (I used port 8888), and the other screen will execute suconnect. I found the shortcuts to use screen here.
Flag
gE269g2h3mw3pwgrj0Ha9Uoqen1c9DGr
Level 21 
Problem 
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Hint 
cron, crontab, crontab(5) (use “man 5 crontab” to access this)
Solution 
Let’s go to the dir in the problem desc, and look at what’s interesting.
bandit21@bandit:~$ cd /etc/cron.d
bandit21@bandit:/etc/cron.d$ ls -la
total 28
drwxr-xr-x 2 root root 4096 Dec 4 01:58 .
drwxr-xr-x 88 root root 4096 Aug 3 2019 ..
-rw-r--r-- 1 root root 189 Jan 25 2017 atop
-rw-r--r-- 1 root root 120 Oct 16 2018 cronjob_bandit22
-rw-r--r-- 1 root root 122 Oct 16 2018 cronjob_bandit23
-rw-r--r-- 1 root root 120 Oct 16 2018 cronjob_bandit24
-rw-r--r-- 1 root root 102 Oct 7 2017 .placeholder
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
After a bit of googling, we can conclude that each line in this file will run the following commands respectively:
- At reboot, run
/usr/bin/cronjob_bandit22.shand redirect both stdout and stderr to/dev/null - Every minute of every hour of every day of every month of every weekday (mon-sun), run the same thing as line 1
So let’s take a look at what the actual script does.
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Looks like the password is outputted into that file in /tmp, let’s see it.
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
Flag
Yk7owGAcWjwMVRwrTesJEwB7WVOiILLI
Level 22 
Problem 
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Hint 
cron, crontab, crontab(5) (use “man 5 crontab” to access this)
Solution 
Let’s look at the cronjob for this level.
bandit22@bandit:/etc/cron.d$ cat cronjob_bandit23
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
Take a look at the shell script.
bandit22@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit23.sh
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget
Try to run it.
bandit22@bandit:/etc/cron.d$ /usr/bin/cronjob_bandit23.sh
Copying passwordfile /etc/bandit_pass/bandit22 to /tmp/8169b67bd894ddbb4412f91573b38db3
Let’s try to see what mytarget variable would be, to do that we’ll run the command that assigns value to the variable. But instead of bandit22 we’ll use bandit23 because that’s the password we’re looking for.
bandit22@bandit:/etc/cron.d$ whoami
bandit22
bandit22@bandit:/etc/cron.d$ echo I am user bandit23 | md5sum | cut -d ' ' -f 1
8ca319486bfbbc3663ea0fbe81326349
bandit22@bandit:/etc/cron.d$ cat /tmp/8ca319486bfbbc3663ea0fbe81326349
jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
Flag
jc1udXuA1tiHqjIsL8yaapX5XIAI6i0n
Level 23 
Problem 
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
Hint 
cron, crontab, crontab(5) (use “man 5 crontab” to access this)
Solution 
Let’s take a look at the cronjob.
bandit23@bandit:/etc/cron.d$ cat cronjob_bandit24
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
Now let’s take a look at the script.
bandit23@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname
echo "Executing and deleting all scripts in /var/spool/$myname:"
for i in * .*;
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
timeout -s 9 60 ./$i
rm -f ./$i
fi
done
It looks a bit wierd at first, so let’s try running it
bandit23@bandit:/etc/cron.d$ /usr/bin/cronjob_bandit24.sh
/usr/bin/cronjob_bandit24.sh: line 5: cd: /var/spool/bandit23: No such file or directory
Executing and deleting all scripts in /var/spool/bandit23:
Handling atop
timeout: failed to run command ‘./atop’: Permission denied
rm: cannot remove './atop': Permission denied
Handling cronjob_bandit22
timeout: failed to run command ‘./cronjob_bandit22’: Permission denied
rm: cannot remove './cronjob_bandit22': Permission denied
Handling cronjob_bandit23
timeout: failed to run command ‘./cronjob_bandit23’: Permission denied
rm: cannot remove './cronjob_bandit23': Permission denied
Handling cronjob_bandit24
timeout: failed to run command ‘./cronjob_bandit24’: Permission denied
rm: cannot remove './cronjob_bandit24': Permission denied
Handling .placeholder
timeout: failed to run command ‘./.placeholder’: Permission denied
rm: cannot remove './.placeholder': Permission denied
Well, after this output, we can more easily figure out that the script will:
- cd to
/var/spool/$mynamewhich would be/var/spool/bandit24because it would be run by bandit24 as indicated in the cronjob - loop through every single file in that dir, and for every file:
- it will try to execute the file
- if it takes more than 60 seconds, kill the file being executed
- then delete it
So now let’s cd into that dir and make a simple script that will just copy the password to a file in a dir in /tmp. I have made the /tmp/asdqweqwe dir for the script to put the password file into.
bandit23@bandit:/var/spool/bandit24$ touch scriptasdqweqwe.sh
bandit23@bandit:/var/spool/bandit24$ nano scriptasdqweqwe.sh
Then in nano, we make this simple shell script.
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/asdqweqwe/pass
Now we have to chmod it so that anyone can execute the script.
bandit23@bandit:/var/spool/bandit24$ chmod 777 scriptasdqweqwe.sh
The trick here, is that our /tmp/asdqweqwe dir must also be chmoded because by default, when you create a dir, only you have write access to it, no one else does. Here’s an example.
bandit23@bandit:/tmp/asdqweqwe$ mkdir asd
bandit23@bandit:/tmp/asdqweqwe$ ls -la
...
drwxr-xr-x 2 bandit23 bandit23 4096 Feb 19 17:30 asd
...
As you can see drwxr-xr-x means that only the owner (which is bandit23) can write into the dir. So we have to chmod our asdqweqwe dir, because our script will be run by bandit24, meaning that bandit24 will write the password file into our dir.
bandit23@bandit:/tmp$ chmod 777 ./asdqweqwe
Now we just wait for the script to run, just about a minute, if you’re impatient you can try to cat your script, if it’s not there anymore, then the cronjob must’ve executed and deleted it. Then we cat the file that we wrote the bandit24 password into.
bandit23@bandit:/var/spool/bandit24$ cat script.sh
cat: script.sh: No such file or directory
bandit23@bandit:/var/spool/bandit24$ cd /tmp/asdqweqwe
bandit23@bandit:/tmp/asdqweqwe$ ls
asd pass
bandit23@bandit:/tmp/asdqweqwe$ cat pass
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ
Flag
UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ
Level 24 
Problem 
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
Solution 
Let’s nmap and see what’s actually running on that port.
bandit24@bandit:~$ nmap localhost -sV -p30002
Starting Nmap 7.40 ( https://nmap.org ) at 2020-02-20 09:54 CET
...
Please\x20enter\x20the\x20password\x20for\x20user\x20bandit24\x20
SF:and\x20the\x20secret\x20pincode\x20on\x20a\x20single\x20line,\x20separa
SF:ted\x20by\x20a\x20space
...
Nmap done: 1 IP address (1 host up) scanned in 142.88 seconds
Full nmap output
bandit24@bandit:~$ nmap localhost -sV -p30002
Starting Nmap 7.40 ( https://nmap.org ) at 2020-02-20 09:54 CET
Completed Service scan at 09:56, 141.12s elapsed (1 service on 1 host)
NSE: Script scanning 127.0.0.1.
Initiating NSE at 09:56
Completed NSE at 09:56, 0.00s elapsed
Initiating NSE at 09:56
Completed NSE at 09:56, 1.26s elapsed
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00017s latency).
PORT STATE SERVICE VERSION
30002/tcp open pago-services2?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port30002-TCP:V=7.40%I=7%D=2/20%Time=5E4E4951%P=x86_64-pc-linux-gnu%r(N
SF:ULL,97,"I\x20am\x20the\x20pincode\x20checker\x20for\x20user\x20bandit25
SF:\.\x20Please\x20enter\x20the\x20password\x20for\x20user\x20bandit24\x20
SF:and\x20the\x20secret\x20pincode\x20on\x20a\x20single\x20line,\x20separa
SF:ted\x20by\x20a\x20space\.\n")%r(GenericLines,F9,"I\x20am\x20the\x20pinc
SF:ode\x20checker\x20for\x20user\x20bandit25\.\x20Please\x20enter\x20the\x
SF:20password\x20for\x20user\x20bandit24\x20and\x20the\x20secret\x20pincod
SF:e\x20on\x20a\x20single\x20line,\x20separated\x20by\x20a\x20space\.\nFai
SF:l!\x20You\x20did\x20not\x20supply\x20enough\x20data\.\x20Try\x20again\.
SF:\nFail!\x20You\x20did\x20not\x20supply\x20enough\x20data\.\x20Try\x20ag
SF:ain\.\n")%r(GetRequest,105,"I\x20am\x20the\x20pincode\x20checker\x20for
SF:\x20user\x20bandit25\.\x20Please\x20enter\x20the\x20password\x20for\x20
SF:user\x20bandit24\x20and\x20the\x20secret\x20pincode\x20on\x20a\x20singl
SF:e\x20line,\x20separated\x20by\x20a\x20space\.\nWrong!\x20Please\x20ente
SF:r\x20the\x20correct\x20current\x20password\.\x20Try\x20again\.\nFail!\x
SF:20You\x20did\x20not\x20supply\x20enough\x20data\.\x20Try\x20again\.\n")
SF:%r(HTTPOptions,105,"I\x20am\x20the\x20pincode\x20checker\x20for\x20user
SF:\x20bandit25\.\x20Please\x20enter\x20the\x20password\x20for\x20user\x20
SF:bandit24\x20and\x20the\x20secret\x20pincode\x20on\x20a\x20single\x20lin
SF:e,\x20separated\x20by\x20a\x20space\.\nWrong!\x20Please\x20enter\x20the
SF:\x20correct\x20current\x20password\.\x20Try\x20again\.\nFail!\x20You\x2
SF:0did\x20not\x20supply\x20enough\x20data\.\x20Try\x20again\.\n")%r(RTSPR
SF:equest,105,"I\x20am\x20the\x20pincode\x20checker\x20for\x20user\x20band
SF:it25\.\x20Please\x20enter\x20the\x20password\x20for\x20user\x20bandit24
SF:\x20and\x20the\x20secret\x20pincode\x20on\x20a\x20single\x20line,\x20se
SF:parated\x20by\x20a\x20space\.\nWrong!\x20Please\x20enter\x20the\x20corr
SF:ect\x20current\x20password\.\x20Try\x20again\.\nFail!\x20You\x20did\x20
SF:not\x20supply\x20enough\x20data\.\x20Try\x20again\.\n")%r(RPCCheck,97,"
SF:I\x20am\x20the\x20pincode\x20checker\x20for\x20user\x20bandit25\.\x20Pl
SF:ease\x20enter\x20the\x20password\x20for\x20user\x20bandit24\x20and\x20t
SF:he\x20secret\x20pincode\x20on\x20a\x20single\x20line,\x20separated\x20b
SF:y\x20a\x20space\.\n");
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 142.88 seconds
We now know that we have to send it in one line separated by a space. We don’t know how to send it though, so let’s try nc.
bandit24@bandit:/tmp/qweqweasd$ nc localhost 30002
I am the pincode checker for user bandit25. Please enter the password for user bandit24 and the secret pincode on a single line, separated by a space.
asd
Fail! You did not supply enough data. Try again.
Now let’s make the script that will bruteforce the 4 digit combination.
#!/bin/bash
for i in {0..9}
do
for j in {0..9}
do
for k in {0..9}
do
for l in {0..9}
do
echo "UoMYTrfrBFHyQXmg6gzctqAwOmw1IohZ ${i}${j}${k}${l}"
done
done
done
done
Now we’ll chmod it so we can actually run it.
bandit24@bandit:/tmp/qweqweasd$ chmod 777 script.sh
Let’s run it into the stdin of nc by piping it.
bandit24@bandit:/tmp/qweqweasd$ ./script.sh | nc localhost 30002
...
Wrong! Please enter the correct pincode. Try again.
Wrong! Please enter the correct pincode. Try again.
Correct!
The password of user bandit25 is uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG
Exiting.
bandit24@bandit:/tmp/qweqweasd$
Flag
uNG9O58gUE7snukf3bvZ0rxhtnjzSGzG
Level 25 
Problem 
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
Hint 
ssh, cat, more, vi, ls, id, pwd
Solution 
Well, we need to know the default shell of bandit26, googling “how to know default shell for ssh user” got me here and found this.
I got curious so I googled “whats in etc passwd file” and got here. Now we know the format of every line in /etc/passwd which is “name, password, user ID, group ID, gecos, home directory, shell”.
bandit25@bandit:~$ cat /etc/passwd | grep bandit26
bandit26:x:11026:11026:bandit level 26:/home/bandit26:/usr/bin/showtext
Looks like the shell is /usr/bin/showtext, looks wierd, let’s see if it’s really a shell
bandit25@bandit:~$ file /usr/bin/showtext
/usr/bin/showtext: POSIX shell script, ASCII text executable
Looks like it’s a shell script, not a shell, so this thing will be run when user bandit26 connects/login to the machine. Let’s take a look at the script.
bandit25@bandit:~$ cat /usr/bin/showtext
#!/bin/sh
export TERM=linux
more ~/text.txt
exit 0
The line export TERM=linux just sets the environment variable TERM to the value linux, googling what that env var does just confuses me and the next line is much more interesting, so instead I googled “how to run shell commands from more” and got to a page which the same as man more, but google highlighted the part “interactive commands” and found this.
v Start up an editor at current line.
Bit of googling for “more vulnerability” eventually made me realize that more will act like cat nothing if the terminal is big enough to display the entire contents of ~/text.txt, and the trick is to resize the terminal so that it’s too small to display the entire file at once, making more actually run.
Here’s how more would run if the terminal is big enough to print out all the contents of ~/text.txt at once.

Now after a bit of googling again, more can be used to call vi which we could then use to read files or execute shell commands.
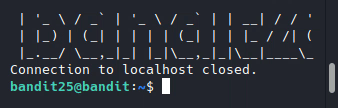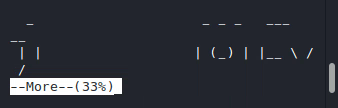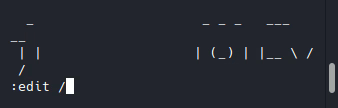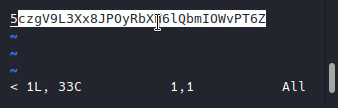
Here I pressed ‘v’ to run vi text editor as indicated in man more, after that, from vi we can edit another file with :edit (found it here), we can’t actually edit the password file but we still can view it’s contents.
Then I tried to set the $SHELL environment variable through running 1 line command in vi with :!, but turns out you can do it with :set.

Flag
5czgV9L3Xx8JPOyRbXh6lQbmIOWvPT6Z
Level 26 
Problem 
Good job getting a shell! Now hurry and grab the password for bandit27!
Hint 
ls
Solution 
Pretty easy once you’ve got the shell from level 25, and already knew about suid binaries like in level 19.
bandit26@bandit:~$ ls
bandit27-do text.txt
bandit26@bandit:~$ file bandit27-do
bandit27-do: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=8e941f24b8c5cd0af67b22b724c57e1ab92a92a1, not stripped
bandit26@bandit:~$ ./bandit27-do
Run a command as another user.
Example: ./bandit27-do id
bandit26@bandit:~$ ls -la
total 36
drwxr-xr-x 3 root root 4096 Oct 16 2018 .
drwxr-xr-x 41 root root 4096 Oct 16 2018 ..
-rwsr-x--- 1 bandit27 bandit26 7296 Oct 16 2018 bandit27-do
-rw-r--r-- 1 root root 220 May 15 2017 .bash_logout
-rw-r--r-- 1 root root 3526 May 15 2017 .bashrc
-rw-r--r-- 1 root root 675 May 15 2017 .profile
drwxr-xr-x 2 root root 4096 Oct 16 2018 .ssh
-rw-r----- 1 bandit26 bandit26 258 Oct 16 2018 text.txt
bandit26@bandit:~$ ./bandit27-do cat /etc/bandit_pass/bandit27
3ba3118a22e93127a4ed485be72ef5ea
Flag
3ba3118a22e93127a4ed485be72ef5ea
Level 27 
Problem 
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo. The password for the user bandit27-git is the same as for the user bandit27.
Hint 
git
Solution 
Clone the repo from the link with git clone.
bandit27@bandit:/tmp/asdqweqwe$ git clone ssh://bandit27-git@localhost/home/bandit27-git/repo
Cloning into 'repo'...
Could not create directory '/home/bandit27/.ssh'.
The authenticity of host 'localhost (127.0.0.1)' can't be established.
ECDSA key fingerprint is SHA256:98UL0ZWr85496EtCRkKlo20X3OPnyPSB5tB5RPbhczc.
Are you sure you want to continue connecting (yes/no)? yes
Failed to add the host to the list of known hosts (/home/bandit27/.ssh/known_hosts).
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit27-git@localhost's password:
remote: Counting objects: 3, done.
remote: Compressing objects: 100% (2/2), done.
remote: Total 3 (delta 0), reused 0 (delta 0)
Receiving objects: 100% (3/3), done.
Try and look inside the repo.
bandit27@bandit:/tmp/asdqweqwe$ ls
repo
bandit27@bandit:/tmp/asdqweqwe$ cd repo
bandit27@bandit:/tmp/asdqweqwe/repo$ ls
README
bandit27@bandit:/tmp/asdqweqwe/repo$ cat README
The password to the next level is: 0ef186ac70e04ea33b4c1853d2526fa2
Flag
0ef186ac70e04ea33b4c1853d2526fa2
Level 28 
Problem 
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo. The password for the user bandit28-git is the same as for the user bandit28.
Hint 
git
Solution 
We clone the repo just like in bandit27.
bandit28@bandit:/tmp/asd28$ git clone ssh://bandit28-git@localhost/home/bandit28-git/repo
Cloning into 'repo'...
...
Resolving deltas: 100% (2/2), done.
bandit28@bandit:/tmp/asd28$ ls
repo
Now when we look inside we only get this “hint”.
bandit28@bandit:/tmp/asd28$ cd repo/
bandit28@bandit:/tmp/asd28/repo$ ls -la
total 16
drwxr-sr-x 3 bandit28 root 4096 Feb 23 10:04 .
drwxr-sr-x 3 bandit28 root 4096 Feb 23 10:04 ..
drwxr-sr-x 8 bandit28 root 4096 Feb 23 10:04 .git
-rw-r--r-- 1 bandit28 root 111 Feb 23 10:04 README.md
bandit28@bandit:/tmp/asd28/repo$ cat README.md
# Bandit Notes
Some notes for level29 of bandit.
## credentials
- username: bandit29
- password: xxxxxxxxxx
bandit28@bandit:/tmp/asd28/repo$
Looks like we have to bruteforce, again? I’m pretty sure we’re not supposed to bruteforce ssh into any of the levels though. Judging by the problem theme, it looks like a git introduction. Checking the password file in /etc/bandit_pass/bandit28 also says that the password file is 33 bytes, so the password length must be the same as other level’s passwords, not 10 chars as indicated by the length of xxxxxxxxxx.
bandit28@bandit:/etc/bandit_pass$ ls -la | grep bandit28
-r-------- 1 bandit28 bandit28 33 Oct 16 2018 bandit28
So how about we try some basic git commands.
bandit28@bandit:/tmp/asd28/repo$ git status
On branch master
Your branch is up-to-date with 'origin/master'.
nothing to commit, working tree clean
bandit28@bandit:/tmp/asd28/repo$ git branch
* master
bandit28@bandit:/tmp/asd28/repo$ git stash list
bandit28@bandit:/tmp/asd28/repo$ git tag
bandit28@bandit:/tmp/asd28/repo$ git log
commit 073c27c130e6ee407e12faad1dd3848a110c4f95
Author: Morla Porla <morla@overthewire.org>
Date: Tue Oct 16 14:00:39 2018 +0200
fix info leak
commit 186a1038cc54d1358d42d468cdc8e3cc28a93fcb
Author: Morla Porla <morla@overthewire.org>
Date: Tue Oct 16 14:00:39 2018 +0200
add missing data
commit b67405defc6ef44210c53345fc953e6a21338cc7
Author: Ben Dover <noone@overthewire.org>
Date: Tue Oct 16 14:00:39 2018 +0200
initial commit of README.md
Looks like there are some commits, let’s go to the previous commit (the one with “add missing data” commit message). We do this with git checkout <commit hash>.
bandit28@bandit:/tmp/asd28/repo$ git checkout 186a1038cc54d1358d42d468cdc8e3cc28a93fcb
Note: checking out '186a1038cc54d1358d42d468cdc8e3cc28a93fcb'.
You are in 'detached HEAD' state. You can look around, make experimental
changes and commit them, and you can discard any commits you make in this
state without impacting any branches by performing another checkout.
If you want to create a new branch to retain commits you create, you may
do so (now or later) by using -b with the checkout command again. Example:
git checkout -b <new-branch-name>
HEAD is now at 186a103... add missing data
bandit28@bandit:/tmp/asd28/repo$ ls
README.md
bandit28@bandit:/tmp/asd28/repo$ cat README.md
# Bandit Notes
Some notes for level29 of bandit.
## credentials
- username: bandit29
- password: bbc96594b4e001778eee9975372716b2
bandit28@bandit:/tmp/asd28/repo$
Now we know how to travel back in time through git!
Flag
bbc96594b4e001778eee9975372716b2
Level 29 
Problem 
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo. The password for the user bandit29-git is the same as for the user bandit29.
Hint 
git
Solution 
Let’s clone it and take a look.
bandit29@bandit:/tmp/asd29$ git clone ssh://bandit29-git@localhost/home/bandit29-git/repo
...
bandit29@bandit:/tmp/asd29$ ls
repo
bandit29@bandit:/tmp/asd29$ cd repo/
bandit29@bandit:/tmp/asd29/repo$ ls -la
total 16
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:32 .
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:32 ..
drwxr-sr-x 8 bandit29 root 4096 Feb 23 14:32 .git
-rw-r--r-- 1 bandit29 root 131 Feb 23 14:32 README.md
bandit29@bandit:/tmp/asd29/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: <no passwords in production!>
bandit29@bandit:/tmp/asd29/repo$
Now let’s test out basic git commands.
bandit29@bandit:/tmp/asd29/repo$ git branch
* master
bandit29@bandit:/tmp/asd29/repo$ git status
On branch master
Your branch is up-to-date with 'origin/master'.
nothing to commit, working tree clean
bandit29@bandit:/tmp/asd29/repo$ git tag
bandit29@bandit:/tmp/asd29/repo$ git stash list
bandit29@bandit:/tmp/asd29/repo$ git log
commit 84abedc104bbc0c65cb9eb74eb1d3057753e70f8
Author: Ben Dover <noone@overthewire.org>
Date: Tue Oct 16 14:00:41 2018 +0200
fix username
commit 9b19e7d8c1aadf4edcc5b15ba8107329ad6c5650
Author: Ben Dover <noone@overthewire.org>
Date: Tue Oct 16 14:00:41 2018 +0200
initial commit of README.md
Let’s take a look at the previous commit.
bandit29@bandit:/tmp/asd29/repo$ git checkout 9b19e7d8c1aadf4edcc5b15ba8107329ad6c5650
Note: checking out '9b19e7d8c1aadf4edcc5b15ba8107329ad6c5650'.
...
HEAD is now at 9b19e7d... initial commit of README.md
bandit29@bandit:/tmp/asd29/repo$ ls -la
total 16
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:34 .
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:32 ..
drwxr-sr-x 8 bandit29 root 4096 Feb 23 14:34 .git
-rw-r--r-- 1 bandit29 root 131 Feb 23 14:34 README.md
bandit29@bandit:/tmp/asd29/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit29
- password: <no passwords in production!>
bandit29@bandit:/tmp/asd29/repo$
Well, we’ve tried all kinds of commands and this is the only other commit, so no other choice but to go in the .git/ folder and take a look at things in there.
bandit29@bandit:/tmp/asd29/repo$ cd .git/
bandit29@bandit:/tmp/asd29/repo/.git$ ls -la
total 52
drwxr-sr-x 8 bandit29 root 4096 Feb 23 14:34 .
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:34 ..
drwxr-sr-x 2 bandit29 root 4096 Feb 23 14:32 branches
-rw-r--r-- 1 bandit29 root 276 Feb 23 14:32 config
-rw-r--r-- 1 bandit29 root 73 Feb 23 14:32 description
-rw-r--r-- 1 bandit29 root 41 Feb 23 14:34 HEAD
drwxr-sr-x 2 bandit29 root 4096 Feb 23 14:32 hooks
-rw-r--r-- 1 bandit29 root 137 Feb 23 14:34 index
drwxr-sr-x 2 bandit29 root 4096 Feb 23 14:32 info
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:32 logs
drwxr-sr-x 4 bandit29 root 4096 Feb 23 14:32 objects
-rw-r--r-- 1 bandit29 root 245 Feb 23 14:32 packed-refs
drwxr-sr-x 5 bandit29 root 4096 Feb 23 14:32 refs
bandit29@bandit:/tmp/asd29/repo/.git$ file *
branches: setgid, directory
config: ASCII text
description: ASCII text
HEAD: ASCII text
hooks: setgid, directory
index: Git index, version 2, 1 entries
info: setgid, directory
logs: setgid, directory
objects: setgid, directory
packed-refs: ASCII text
refs: setgid, directory
bandit29@bandit:/tmp/asd29/repo/.git$ cat *
cat: branches: Is a directory
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[remote "origin"]
url = ssh://bandit29-git@localhost/home/bandit29-git/repo
fetch = +refs/heads/*:refs/remotes/origin/*
[branch "master"]
remote = origin
merge = refs/heads/master
Unnamed repository; edit this file 'description' to name the repository.
9b19e7d8c1aadf4edcc5b15ba8107329ad6c5650
cat: hooks: Is a directory
DIRC^Rs1�v#^Rs1�v#�
Ƒ��+�-���fQD@��r�ƫ�i� README.mdTREE1 0
�Gm�L�RL�I���*^xq[D�Y����x�;�1:0I��5^cat: info: Is a directory
cat: logs: Is a directory
cat: objects: Is a directory
# pack-refs with: peeled fully-peeled
33ce2e95d9c5d6fb0a40e5ee9a2926903646b4e3 refs/remotes/origin/dev
84abedc104bbc0c65cb9eb74eb1d3057753e70f8 refs/remotes/origin/master
2af54c57b2cb29a72e8f3e84a9e60c019c252b75 refs/remotes/origin/sploits-dev
cat: refs: Is a directory
bandit29@bandit:/tmp/asd29/repo/.git$
We found something, on the line with # pack-refs, what looks like commit hashes. But first let’s find out where that actually is, from tha file * output we only see some ASCII text files, so let’s try those out.
bandit29@bandit:/tmp/asd29/repo/.git$ file * | grep ASCII
config: ASCII text
description: ASCII text
HEAD: ASCII text
packed-refs: ASCII text
bandit29@bandit:/tmp/asd29/repo/.git$ cat config
...
bandit29@bandit:/tmp/asd29/repo/.git$ cat description
...
bandit29@bandit:/tmp/asd29/repo/.git$ cat HEAD
...
bandit29@bandit:/tmp/asd29/repo/.git$ cat packed-refs
# pack-refs with: peeled fully-peeled
33ce2e95d9c5d6fb0a40e5ee9a2926903646b4e3 refs/remotes/origin/dev
84abedc104bbc0c65cb9eb74eb1d3057753e70f8 refs/remotes/origin/master
2af54c57b2cb29a72e8f3e84a9e60c019c252b75 refs/remotes/origin/sploits-dev
bandit29@bandit:/tmp/asd29/repo/.git$
Looks like it’s the packed-refs file. Little bit of googling got me here which tells me that this file is for storing dormant/deserted refs (refs are pretty much like a branch). There’s only 3 of them, and we know the 2nd ref is the branch we are currently in (master branch), so let’s try the “dev” branch.
bandit29@bandit:/tmp/asd29/repo$ git checkout 33ce2e95d9c5d6fb0a40e5ee9a2926903646b4e3
Previous HEAD position was 9b19e7d... initial commit of README.md
HEAD is now at 33ce2e9... add data needed for development
bandit29@bandit:/tmp/asd29/repo$ ls -la
total 20
drwxr-sr-x 4 bandit29 root 4096 Feb 23 14:43 .
drwxr-sr-x 3 bandit29 root 4096 Feb 23 14:32 ..
drwxr-sr-x 2 bandit29 root 4096 Feb 23 14:43 code
drwxr-sr-x 8 bandit29 root 4096 Feb 23 14:43 .git
-rw-r--r-- 1 bandit29 root 134 Feb 23 14:43 README.md
bandit29@bandit:/tmp/asd29/repo$ cat README.md
# Bandit Notes
Some notes for bandit30 of bandit.
## credentials
- username: bandit30
- password: 5b90576bedb2cc04c86a9e924ce42faf
bandit29@bandit:/tmp/asd29/repo$
The code/ folder is just filled with a dummy file.
Flag
5b90576bedb2cc04c86a9e924ce42faf
Level 30 
Problem 
There is a git repository at ssh://bandit30-git@localhost/home/bandit30-git/repo. The password for the user bandit30-git is the same as for the user bandit30.
Hint 
git
Solution 
Clone the repo and take a look.
bandit30@bandit:/tmp/asd30$ git clone ssh://bandit30-git@localhost/home/bandit30-git/repo
...
bandit30@bandit:/tmp/asd30$ ls
repo
bandit30@bandit:/tmp/asd30$ cd repo/
bandit30@bandit:/tmp/asd30/repo$ ls -la
total 16
drwxr-sr-x 3 bandit30 root 4096 Feb 23 14:45 .
drwxr-sr-x 3 bandit30 root 4096 Feb 23 14:45 ..
drwxr-sr-x 8 bandit30 root 4096 Feb 23 14:45 .git
-rw-r--r-- 1 bandit30 root 30 Feb 23 14:45 README.md
bandit30@bandit:/tmp/asd30/repo$ cat README.md
just an epmty file... muahaha
Very funny, let’s do basic git commands again.
bandit30@bandit:/tmp/asd30/repo$ git branch
* master
bandit30@bandit:/tmp/asd30/repo$ git tag
secret
bandit30@bandit:/tmp/asd30/repo$ git log
commit 3aa4c239f729b07deb99a52f125893e162daac9e
Author: Ben Dover <noone@overthewire.org>
Date: Tue Oct 16 14:00:44 2018 +0200
initial commit of README.md
bandit30@bandit:/tmp/asd30/repo$ git status
On branch master
Your branch is up-to-date with 'origin/master'.
nothing to commit, working tree clean
bandit30@bandit:/tmp/asd30/repo$
Looks see if there’s something in the secret tag. We use the git show <tagname> command.
bandit30@bandit:/tmp/asd30/repo$ git show secret
47e603bb428404d265f59c42920d81e5
Now let’s checkout into that branch and take a look.
bandit30@bandit:/tmp/asd30/repo$ git checkout 47e603bb428404d265f59c42920d81e5
error: pathspec '47e603bb428404d265f59c42920d81e5' did not match any file(s) known to git.
Ok, that hash isn’t a ref, so… maybe it’s actually the password to the next level?
*tries it out*
Wow it actually is, didn’t think it’d be this easy considering the previous level.
Flag
47e603bb428404d265f59c42920d81e5
Level 31 
Problem 
There is a git repository at ssh://bandit31-git@localhost/home/bandit31-git/repo. The password for the user bandit31-git is the same as for the user bandit31.
Hint 
git
Solution 
Clone and take a lookie.
bandit31@bandit:/tmp/asd31$ git clone ssh://bandit31-git@localhost/home/bandit31-git/repo
...
bandit31@bandit:/tmp/asd31$ ls
repo
bandit31@bandit:/tmp/asd31$ cd repo/
bandit31@bandit:/tmp/asd31/repo$ ls -la
total 20
drwxr-sr-x 3 bandit31 root 4096 Feb 23 15:37 .
drwxr-sr-x 3 bandit31 root 4096 Feb 23 15:37 ..
drwxr-sr-x 8 bandit31 root 4096 Feb 23 15:37 .git
-rw-r--r-- 1 bandit31 root 6 Feb 23 15:37 .gitignore
-rw-r--r-- 1 bandit31 root 147 Feb 23 15:37 README.md
bandit31@bandit:/tmp/asd31/repo$ cat README.md
This time your task is to push a file to the remote repository.
Details:
File name: key.txt
Content: 'May I come in?'
Branch: master
bandit31@bandit:/tmp/asd31/repo$ cat .gitignore
*.txt
So we’re supposed to3 push a txt file to the master branch, but the .gitignore file is going to ignore all files that match the regex *.txt so let’s
- delete the
.gitignorefile, - make the
key.txtfile, - write the contents, and then
- push the changes into the master branch.
bandit31@bandit:/tmp/asd31/repo$ rm -f .gitignore
bandit31@bandit:/tmp/asd31/repo$ echo "May I come in?" > key.txt
bandit31@bandit:/tmp/asd31/repo$ git add .
bandit31@bandit:/tmp/asd31/repo$ git commit -m 'test'
[master 68fa52f] test
2 files changed, 1 insertion(+), 1 deletion(-)
delete mode 100644 .gitignore
create mode 100644 key.txt
bandit31@bandit:/tmp/asd31/repo$ git push
...
bandit31-git@localhost's password:
Counting objects: 3, done.
Delta compression using up to 4 threads.
Compressing objects: 100% (2/2), done.
Writing objects: 100% (3/3), 281 bytes | 0 bytes/s, done.
Total 3 (delta 0), reused 0 (delta 0)
remote: ### Attempting to validate files... ####
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
remote: Well done! Here is the password for the next level:
remote: 56a9bf19c63d650ce78e6ec0354ee45e
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
To ssh://localhost/home/bandit31-git/repo
! [remote rejected] master -> master (pre-receive hook declined)
error: failed to push some refs to 'ssh://bandit31-git@localhost/home/bandit31-git/repo'
bandit31@bandit:/tmp/asd31/repo$
We successfully pushed our changes, it was rejected so that the problem would remain the same for other users, and we got the password in the reject message.
Flag
56a9bf19c63d650ce78e6ec0354ee45e
Level 32 
Problem 
After all this git stuff its time for another escape. Good luck!
Hint 
sh, man
Solution 
After logging in, it looks like everything we type will be converted to uppercase before being sent to the sh shell.
ssh bandit32@bandit.labs.overthewire.org -p 2220
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit32@bandit.labs.overthewire.org's password:
...
WELCOME TO THE UPPERCASE SHELL
>> ls
sh: 1: LS: not found
>> pwd
sh: 1: PWD: not found
>> bash
sh: 1: BASH: not found
>>
Let’s try to ssh and request for another shell.
ssh -t bandit32@bandit.labs.overthewire.org -p 2220 /bin/bash
This is a OverTheWire game server. More information on http://www.overthewire.org/wargames
bandit32@bandit.labs.overthewire.org's password:
WELCOME TO THE UPPERCASE SHELL
>> ls
sh: 1: LS: not found
Looks like we still fall into the sh shell. After quite a bit of googling about hwo to convert uppercase shellscript into lowercase with sh and not bash, I decided to read about shellscripts until I came across the topic of variables and it turns out $0 is the name of the executable/script that is currently running.
From the errors (e.g. sh: 1: LS: not found) we know that the real shell is th plain sh shell and not this uppercase shell, and whatever we input, the uppercase shell will try to execute it. So by calling $0 we are calling /bin/sh, the real one, to be executed by the modified shell we are currently in. Thankfully /bin/sh doesn’t get uppercased, so it actually gets spawned.
>> $PWD
sh: 1: /home/bandit32: Permission denied
>> $0
$ echo $0
sh
$ cat /etc/bandit_pass/bandit33
c9c3199ddf4121b10cf581a98d51caee
$
Here we can see when I input $PWD, the value in the variable (which is /home/bandit32) was attempted to be exececuted, so the same must apply to $0 which is why we successfully spawned the shell.
Flag
c9c3199ddf4121b10cf581a98d51caee
Level 33 
Problem 
At this moment, level 34 does not exist yet.
Solution 
bandit33@bandit:~$ ls
README.txt
bandit33@bandit:~$ cat README.txt
Congratulations on solving the last level of this game!
At this moment, there are no more levels to play in this game. However, we are constantly working
on new levels and will most likely expand this game with more levels soon.
Keep an eye out for an announcement on our usual communication channels!
In the meantime, you could play some of our other wargames.
If you have an idea for an awesome new level, please let us know!
Flag
We did it! ![]()
Takeaway 
- Don’t be lazy and read the man page