Problem 
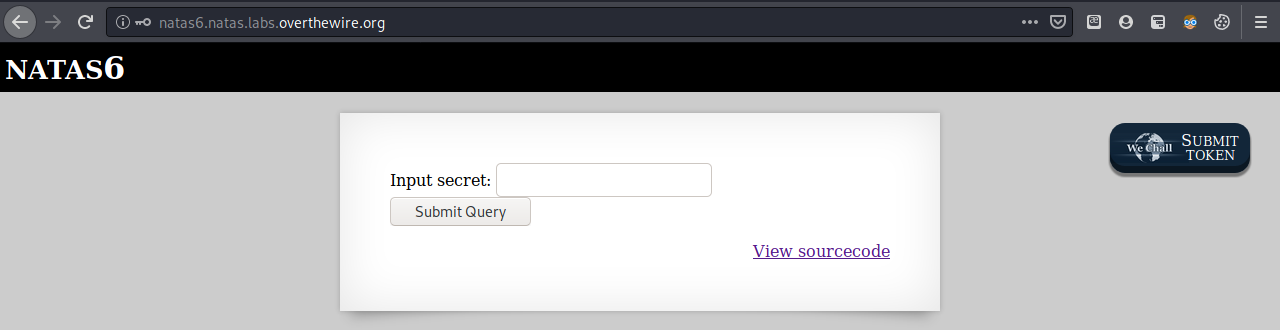
We arrive at a webpage that asks for a query.
Solution 
If you put a random string in, it just says “Wrong secret”, so let’s look at the source.
Full PHP Code Snippet
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>
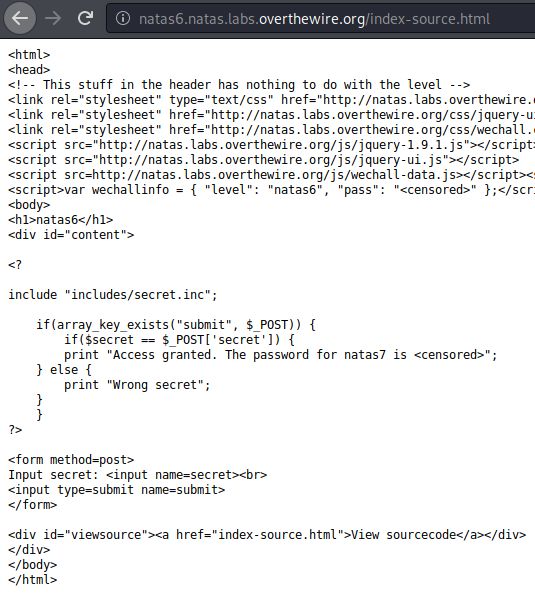
From the snippet above, we can conclude that we need to input a string that has the same value as the $secret var. We don’t see that var getting initialized or having a value assigned to it in this page, but there is another file that is being included which is secret.inc located in includes/ so let’s try to access it.
Notice that the code won’t be displayed because it’s not html, so we have to view the page source (or “inspect” the page). As to why we can see PHP code here but not on other PHP pages, I found this explanation.
… servers normally are not configured to parse .inc files as php, so if the file sits in your web root and your server is configured in the default way, a user could view your php source code in the .inc file by visiting the URL directly …
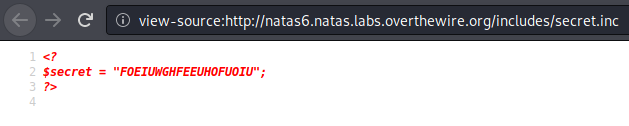
Now we know why we can see the .inc source code. Now to submit the string! Upon submitting FOEIUWGHFEEUHOFUOIU as found in secret.inc, we get the flag.
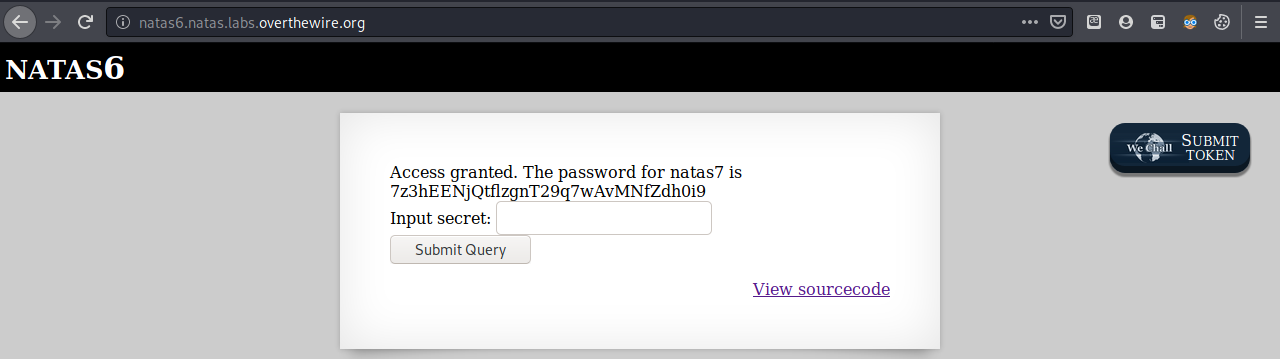
Flag 
7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
Takeaway 
- Always try and see what’s inside files with wierd extensions
| ‹ Previous in Web exploitation: Natas5 | Next in Web exploitation: Natas7 › |