Problem 
We found this packet capture. Recover the flag.
Hint 
Try using a tool like Wireshark
What are streams?
Solution 
First let’s see if we do strings on the file.
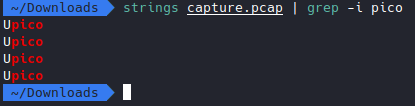
Well, not the flag, but could be something, now let’s open it up in wireshark.
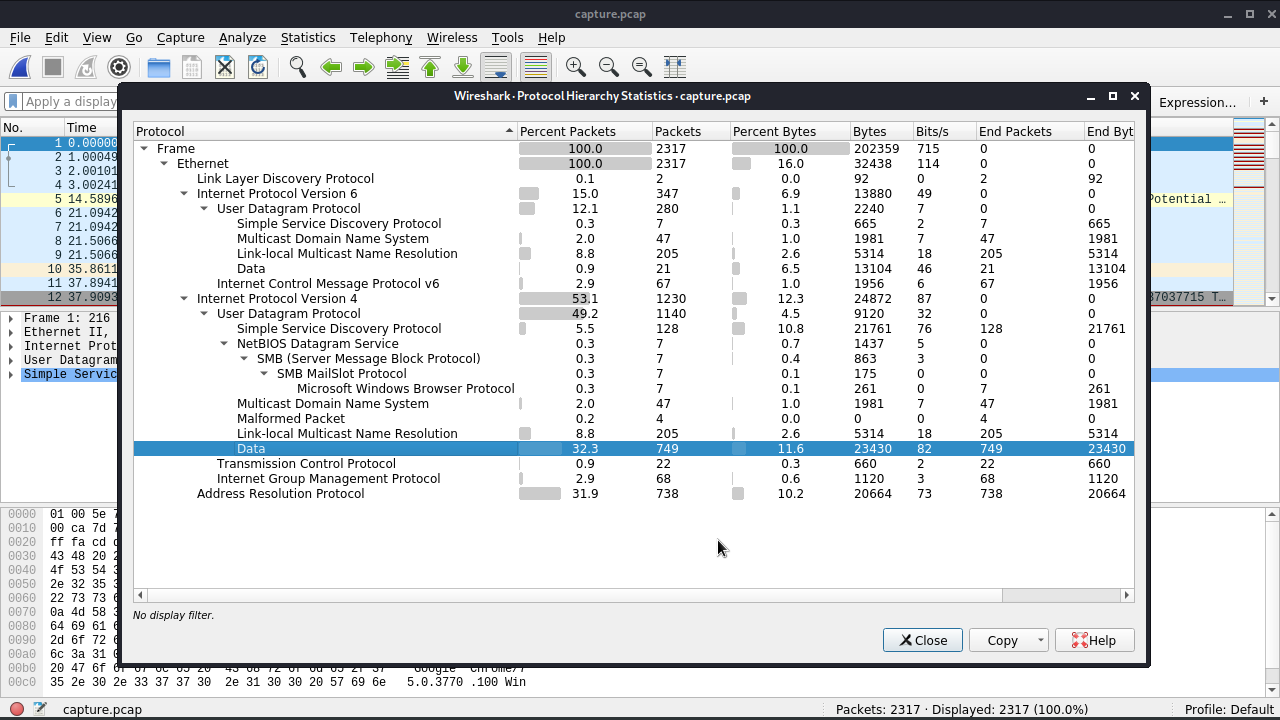
We look at “Statistics > Protocol Hierarchy”, and based on what we got from strings which is Upico, let’s assume it’s a hint pointing to the UDP protocol, so we set the UDP data as a filter.
As we scroll through, let’s look at the “data” section of the packet (the one highlighted blue) and we will see that it’s sending the word “pico” 1 char at a time (1 char per packet).
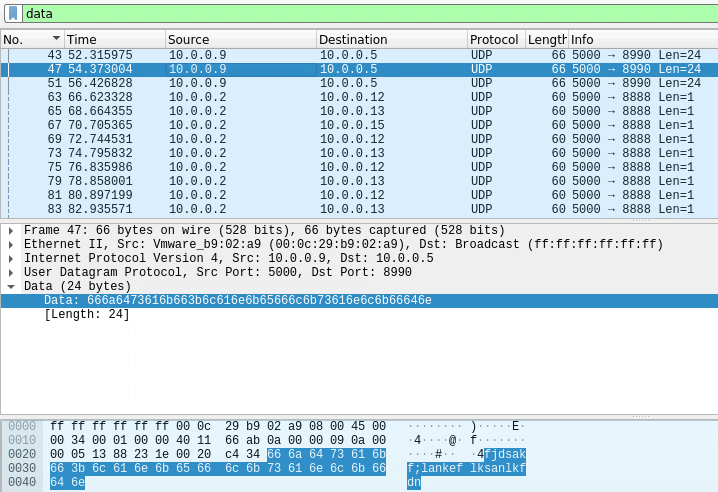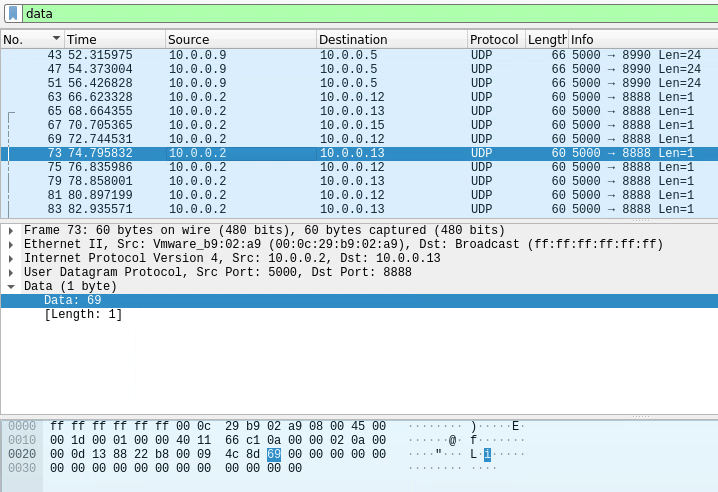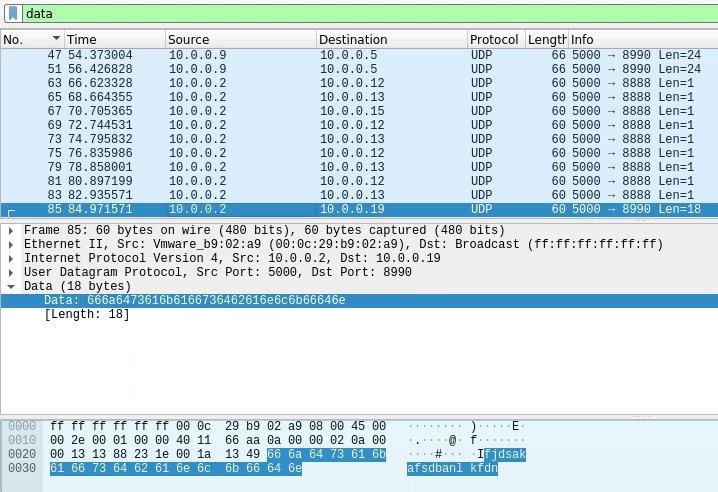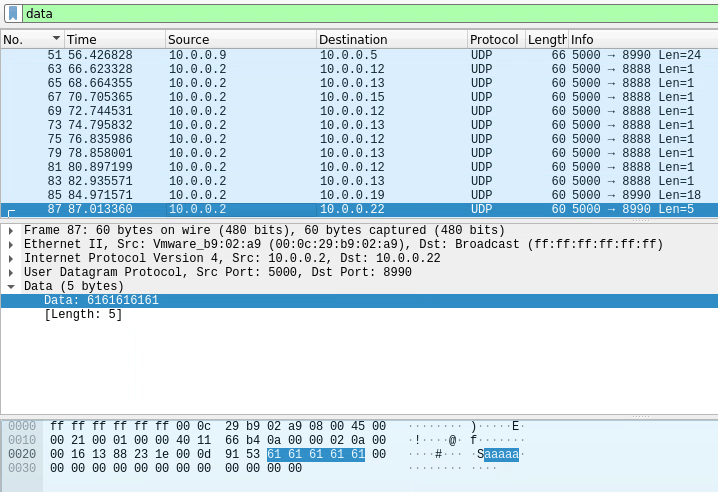
There’s also another letter on the left of it, so let’s click it to see what section of the packet it is supposed to be.
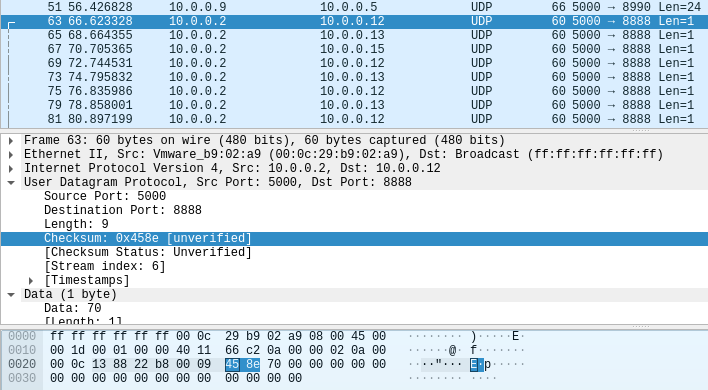
So it’s just a checksum for the packet, pretty sure it’s not useful, so let’s follow the stream that starts with the p char.
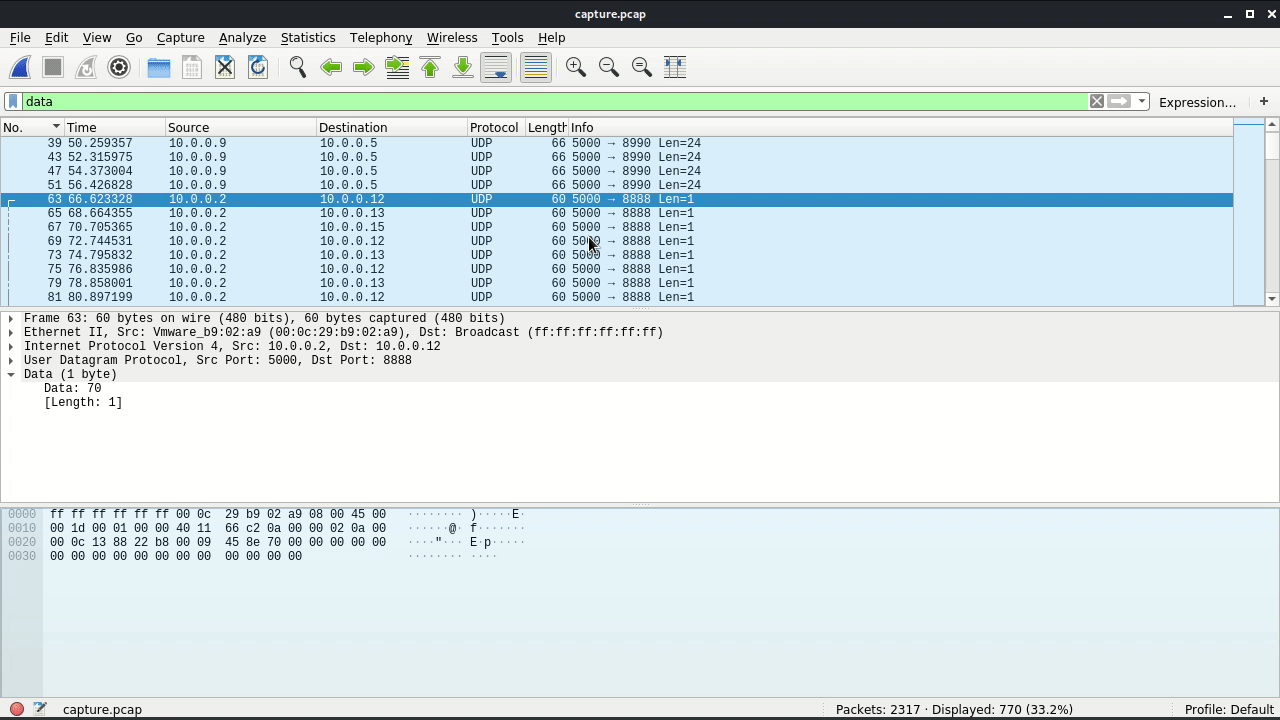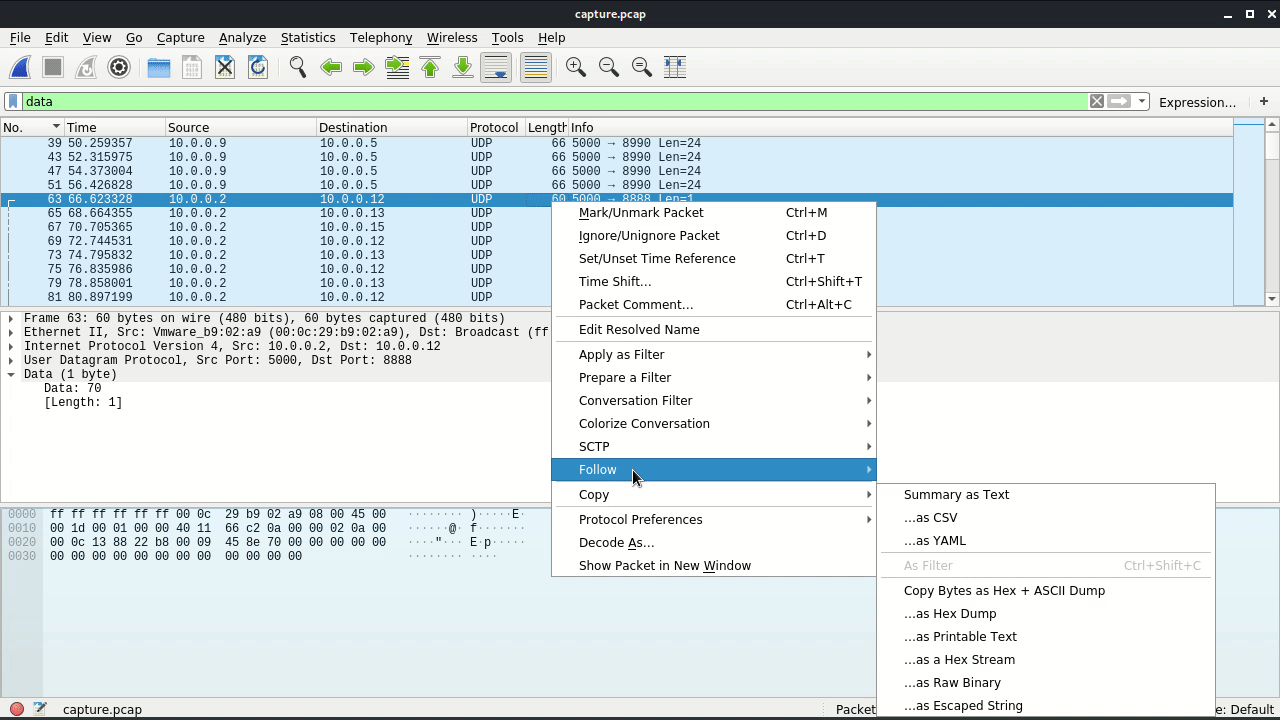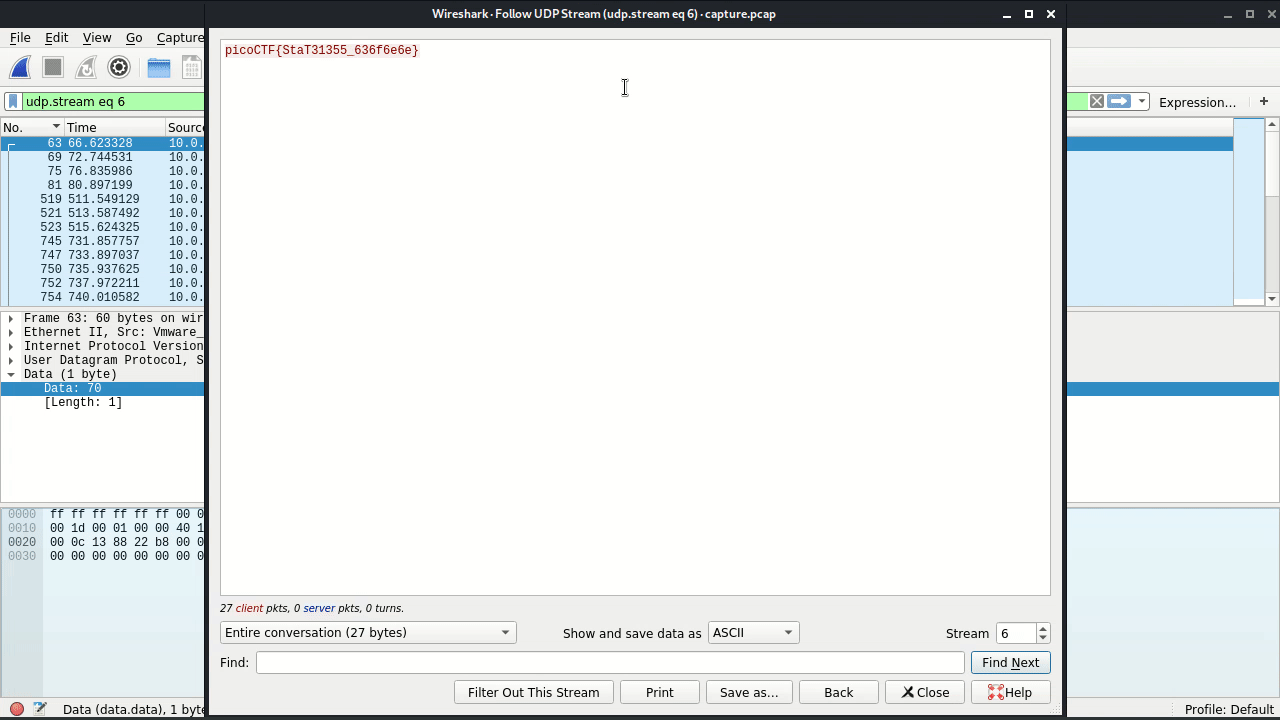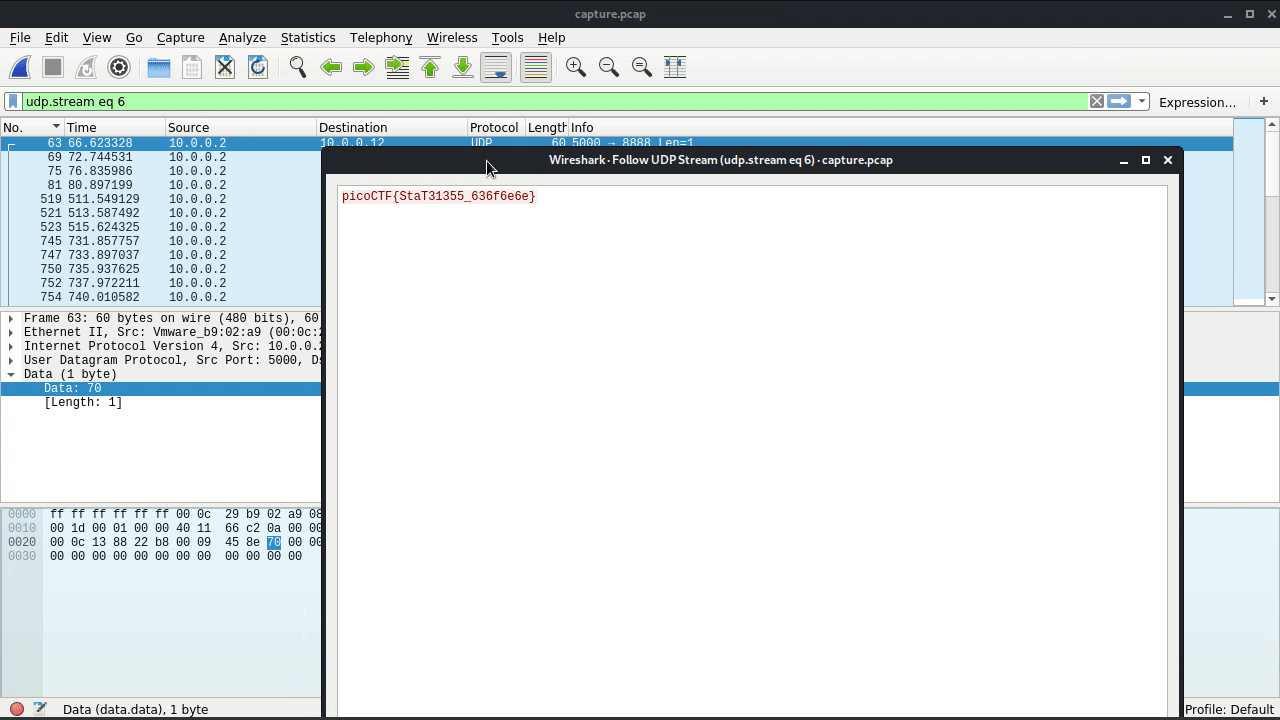
Turns out it actually is the stream that’s sending the flag, 1 char per packet.
Flag 
picoCTF{StaT31355_636f6e6e}
| ‹ Previous in Forensics: What Lies Within |